Subscribe to our blog
Thanks for subscribing to the blog.
August 16, 2021
Topics: Cloud Volumes ONTAP AzureDisaster RecoveryAdvanced11 minute read
Having the right DR strategy is an important way to make sure the lights stay on should a disaster strike your application hosting environment. While cloud-based DRaaS solutions offer easy-to-deploy, and simplified alternatives to costly on-premises DR solutions, they may not give enterprise users all the platform flexibility they need.
Cloud Volumes ONTAP provides efficient and reliable DR capabilities in AWS, Azure, and Google Cloud. This blog will provide step-by-step instructions on how to deploy and configure a disaster recovery solution in Azure using Cloud Volumes ONTAP.
Use the links below to jump down to each step of the set-up process:
- Cloud Volumes ONTAP and Azure Disaster Recovery
- Start the BlueXP Console
- Discover an On-Premises Environment
- Create a New Cloud Volumes ONTAP Environment in Azure
- Create a Replication Relationship
- Monitor and Manage the Replication Relationship
- Conclusion
Cloud Volumes ONTAP and Azure Disaster Recovery
Cloud Volumes ONTAP helps in Azure disaster recovery by providing an easy-to-deploy, storage-efficient, enterprise-class DR solution. The benefits of using Cloud Volumes ONTAP for DR include:
- Easy data replication from on-premises to a DR site in Azure.
- Quick storage failover and failback.
- Storage optimization technologies and automated data tiering to Azure Blob help reduce storage footprint and costs.
Configuration Prerequisites
To begin with, you’ll need to have NetApp BlueXP Console. If you haven’t used Cloud Manager yet, follow these instructions on how to set up your Azure subscription and Cloud Volumes ONTAP environment. Note that you can also use NetApp BlueXP for centralized access of NetApp cloud services including BlueXP Console.
Network Prerequisites
To replicate volumes from an on-premises environment to the cloud for DR purposes, we need to establish network connectivity to Azure, either using a site-to-site VPN or ExpressRoute. ExpressRoute is a dedicated private connection from an on-premises network to Azure VNET, facilitated by a service provider. VPN, on the other hand, is a less expensive option of establishing hybrid connectivity through an encrypted channel over the internet.
In this section we’ll show how to create a network with required inbound and outbound permissions and then configure a VPN to establish connectivity with the on-premises environment.
- First off, we need to create a VNet.
From the Azure portal, select Virtual Networks > click “+Create” and provide the network details such as name, resource group, region and VNet name. Click on “Next:IP Addresses”:
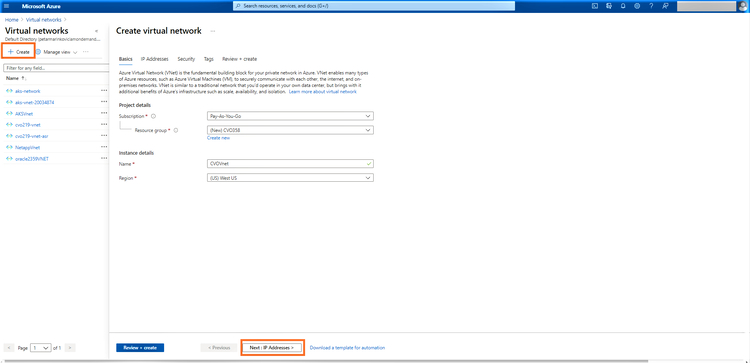
2.In this step, provide the VNet address space and subnets. You can use the default IP range given or add a new range.
Once done, click on “Next:Security”:
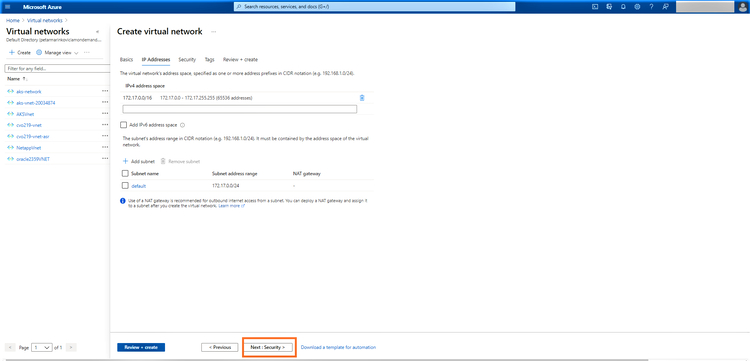
3.In the next step, choose options for bastion host, DDOS standard, and firewall. For the purposes of this demo, we will use the default configuration.
Click on “Next:Tags” to proceed: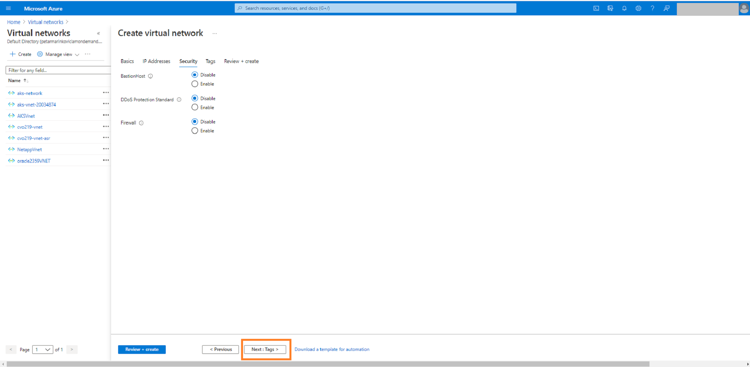
4.In this step you may add tags, if you have any. Tags can be useful for organizing your volumes.
When you’re done, click on “Next: Review + create”:
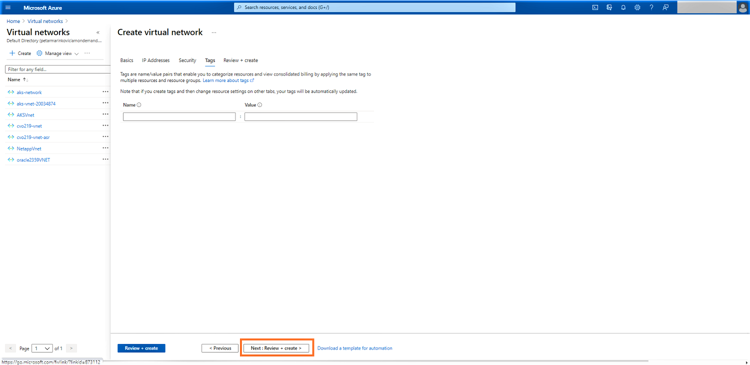
5. Click on “Create” to deploy the VNet: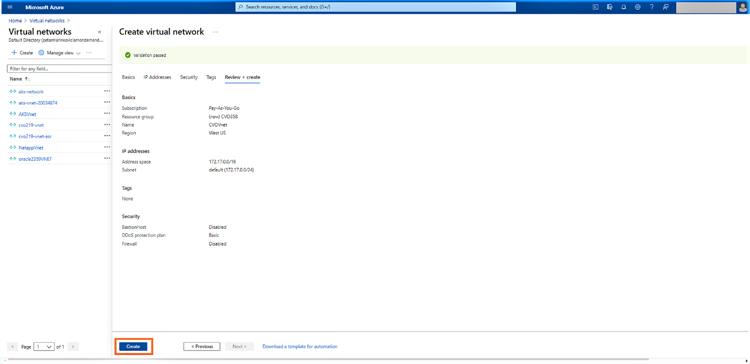
6. Next, we are going to create a gateway subnet. The VPN gateway required for enabling connectivity between the on-premises environment and Azure will be deployed to this gateway subnet in the Azure VNet.
For DR purposes, we will be replicating data from on-premises (or another cloud) to Cloud Volumes ONTAP in Azure using SnapMirror® technology. For that reason, your VPN should be created from the VNET to the on-premises environment.
Open the VNet created in the previous step from the Azure portal and click on “+ Gateway subnet”: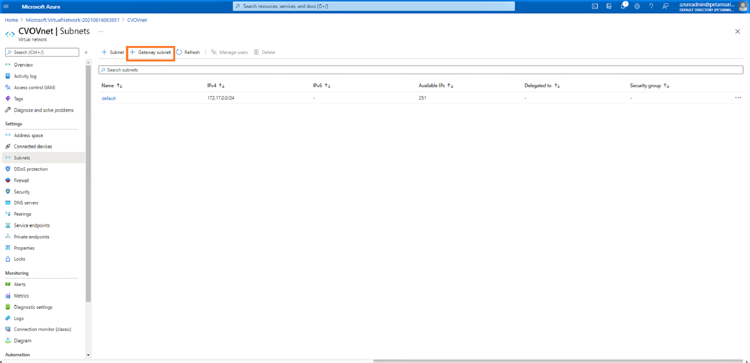
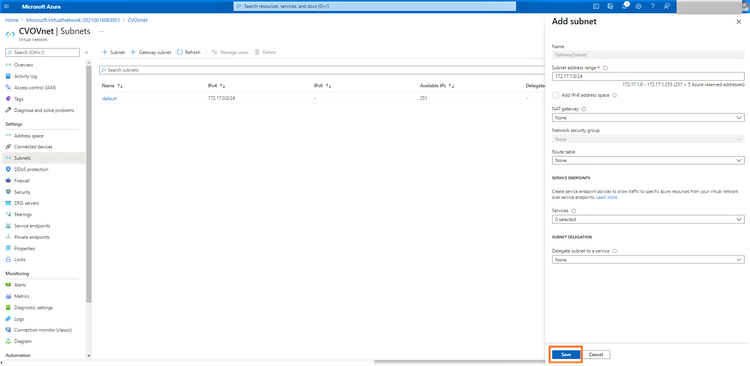
7. You can choose to use the default address range listed in the window or adjust it as per your network requirements. Click “Save” to create the gateway subnet:
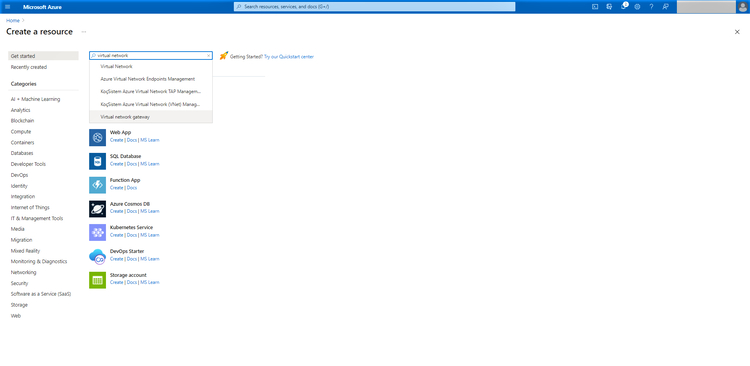
8. In the Azure portal click on “+Create a resource” and search for “Virtual network gateway”:
9.Click on “Create”:
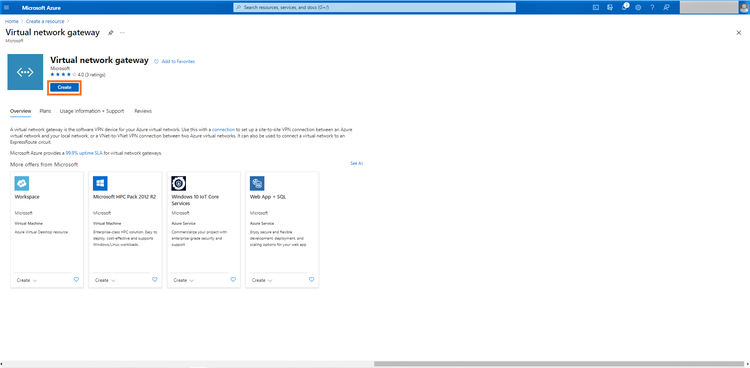
10. In the Virtual network gateway creation wizard, provide the following details:
- Select your subscription from the drop-down menu.
- Name of the gateway.
- Azure region where the gateway will be deployed. Note that it should be the same region as the region used by the VNet we created in Step 5.
- Select “VPN” as the gateway type.
- For VPN type, select “Route based.” (“Policy-based” should be selected only if your on-premises perimeter device does not support route-based VPN.)
- Select a VPN SKU based on your aggregate VPN throughput requirements. Minimum VpnGw2 SKU is recommended as it provides a throughput of 1 Gbps but note that it would be dependent on your internet service provider’s throughput as well.
- Select the generation of the gateway depending on the SKU selected
- Select the virtual network that we created in Step 5.
- Create a new public IP if you don’t have an existing one.
- Give the public IP a name.
- The remaining settings can be configured to be default and click on “Next:Tags”
11. In this step you have the option to add tags relevant to your Azure environment.
Click on "Next: Review + Create":
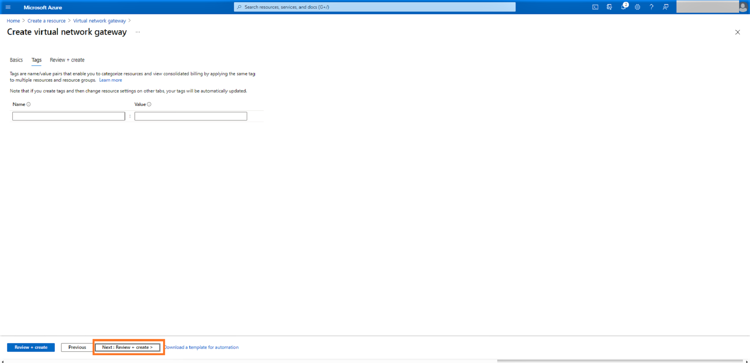
12. Once the validation is successful, click on “Create” to create the Virtual Network Gateway:
Note that this creation process may take up to 45 minutes to complete.
13. Now that the VPN gateway is set up, we need to create a local network gateway that represents your on-premises VPN endpoint and the IP range of the on-premises network that will be connected to Azure VNet.
Open the newly created gateway. Go to Settings > Connections, and click “Add”:
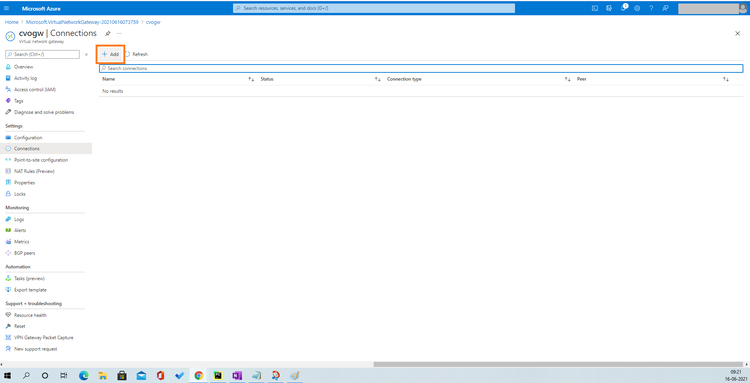
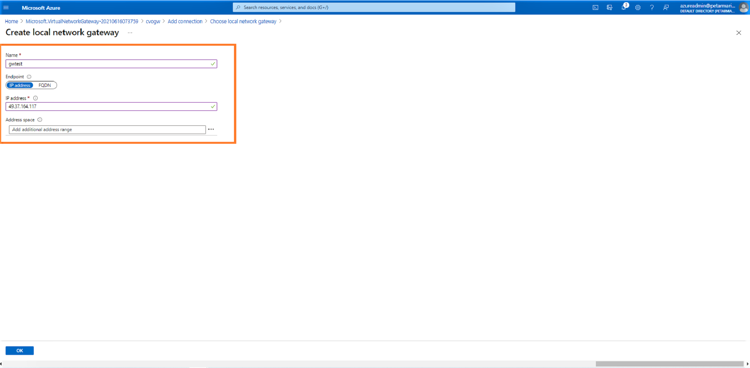
14. Provide the name of the connection. Click on Choose a local gateway > Create new.
Select connection type as “Site to Site (IPsec)” and provide details of your on-premises VPN device, including the name to identify the device, public IP, and the local network IP range. Then click “OK”:
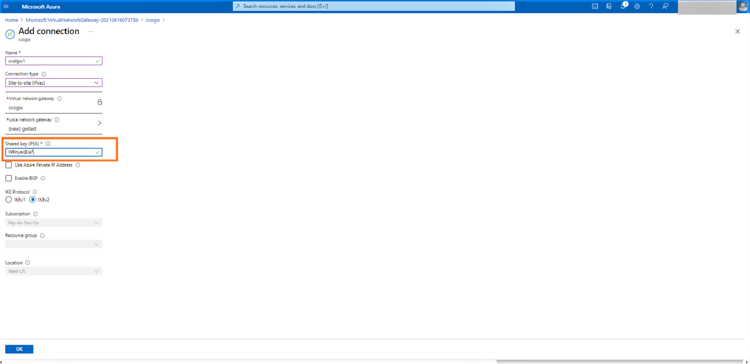
15. Provide a shared key which will be used to encrypt the communication between your on-premises VPN device and Azure VPN gateway. It can be the key provided by your on-premises device or you can create one here and use the same in your local VPN device. Click “OK” to create the connection:
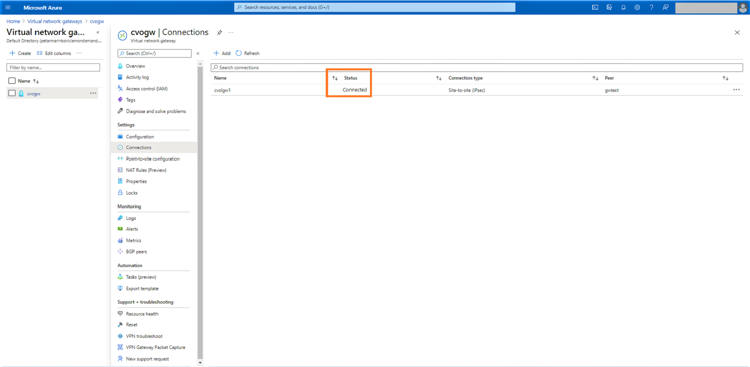
16. Open the Virtual network gateway > connections, click on the connection created in the step above, and verify that the status is “connected”:
With that step, your network prerequisites should all be complete. You can now move on to using BlueXP Console.
Start BlueXP Console
Log in to your NetApp BlueXP account and see the “Fabric View” screen.
Find the Cloud Volumes ONTAP tab and select “Go to BlueXP Console”.
Once you login to BlueXP Console, you'll get to the Canvas screen, where you can see your current working environments:
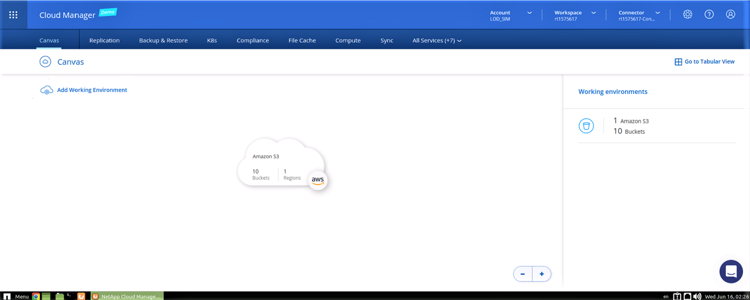
Discover an On-Premises Environment
1. Click on “+Add Working Environments” to start a new environment:
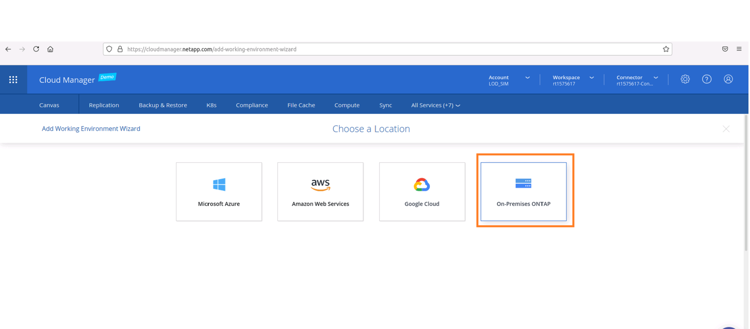
2. Select "On-Premises ONTAP":
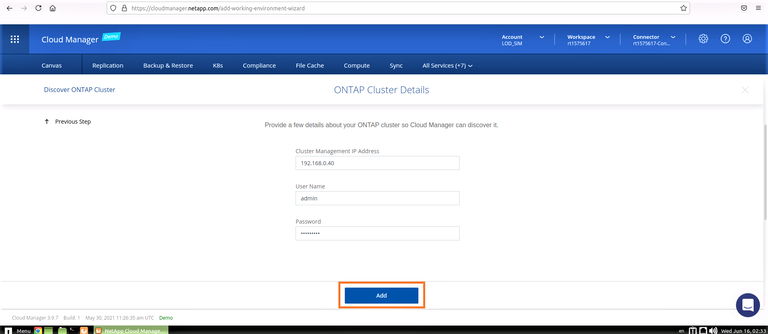
3. Enter the on-premises cluster management IP details and admin credentials and click on “Add”:
4. Click “Go” to discover the on-premises ONTAP system. Once the Discover operation is completed, you’ll see the new on-Prem environment in your working environments in BlueXP Console.
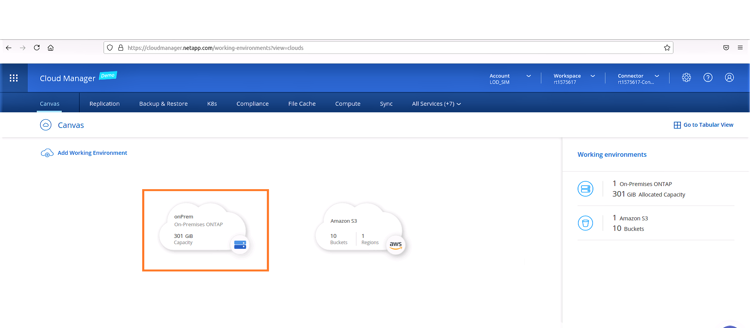
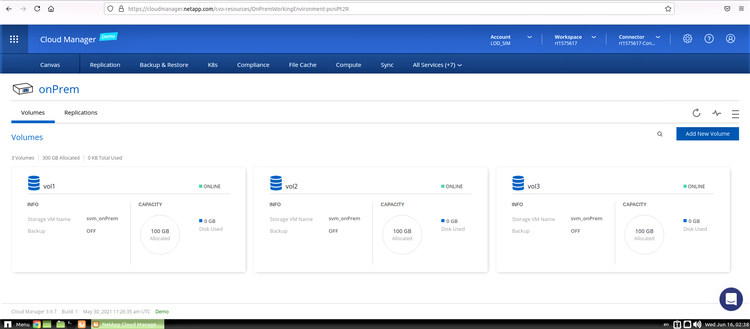
5. Double-click the discovered cluster to see the volumes and determine which one you wish to replicate.
Create a New Cloud Volumes ONTAP Environment in Azure
Click the “Add a Working Environment” on the BlueXP Console main screen. This will start a wizard that will guide you step by step in the process.
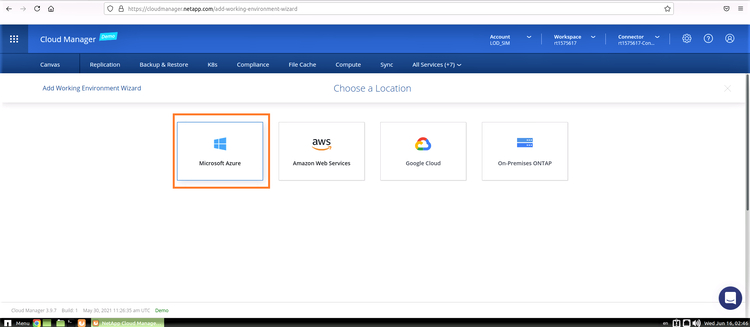
1. In the first step you will choose the cloud in which you wish to start your new environment.
The available options are AWS, Azure, and Google Cloud, in a single-node or high availability configuration. Click on Microsoft Azure:
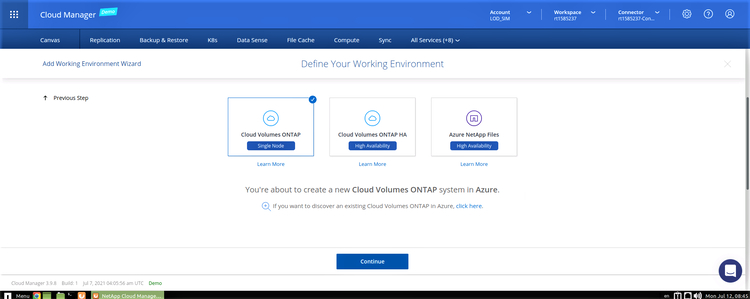
2. For this scenario, we are selecting the “Cloud Volumes ONTAP Single Node” option for Azure. Select the option and click “Continue”:
3. In this step you will provide the details of the environment to be created including the environment name and admin credentials. Add resource group tags for the Azure environment as an optional parameter.
When you are finished, click “Continue.”
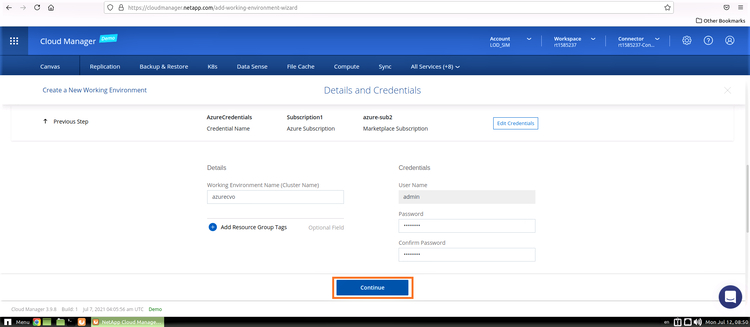
4. In this step you can select the add-on services for your Cloud Volumes ONTAP deployment, including Cloud Data Sense, Cloud Backup, and Cloud Insights. Select the services you wish to use, and then click “Continue”:
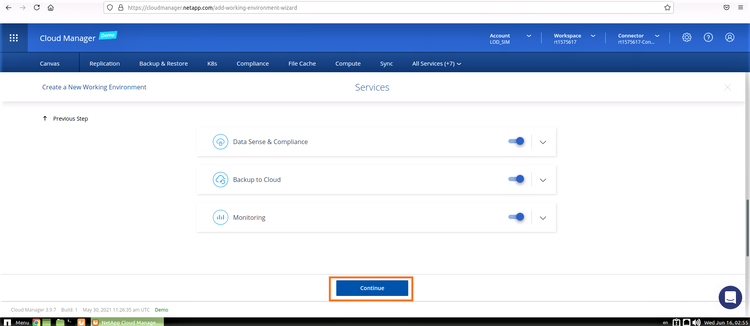
5. In this step, configure the Azure location and connectivity. Select the Azure Region, resource group, VNet, and subnet to be used, such as the one created in the steps outlined above.
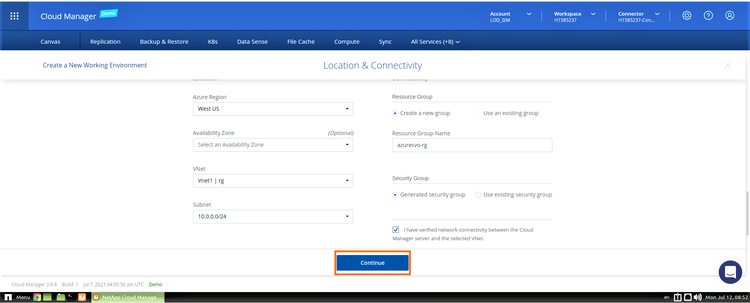
If you choose to create a new security group, BlueXP Console will create a group with all required inbound/outbound access rules. Alternatively, you can choose an existing security group (click here for the documentation about which ports are needed).
You should also confirm that connectivity exists between BlueXP Console Server and the selected VNet. Click “Continue.”
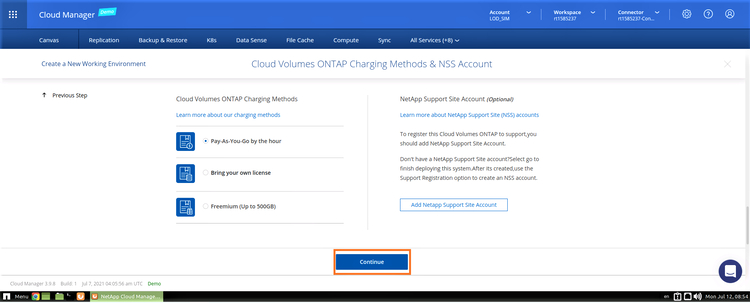
6. In this screen, choose your license option: Pay-As-You-Go or BYOL if you want to use an existing license.
Optionally, you can also select a NetApp Support Site (NSS) account to be used with the configuration.
An NSS account is recommended for the Pay-As-You-Go option to activate support for your system. Note that the NSS account can be added later as well.
Activation provides access to NetApp technical support resources and software updates. For the BYOL option, an NSS account allows you to upload your license key and enable the subscription for the term that you purchased. This includes automatic updates for term renewals.
In this example, we will keep the default Pay-As-You-Go option.
7. In this step, you can choose between several preconfigured packages available for various types of workloads.
These options include database and application data production workloads and high-performance production workloads. You can hover over each option to view the configuration parameters of each option.
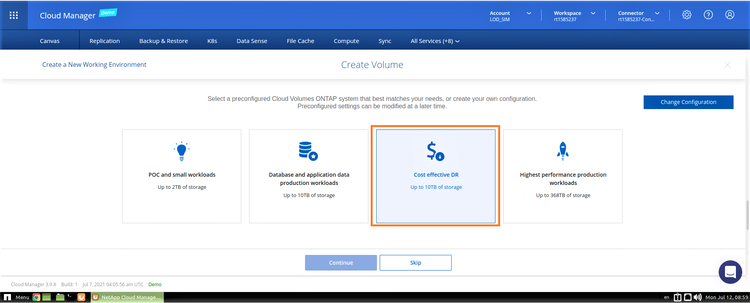
Alternatively, you can click the “Change configuration” button in the top-right corner of the screen to create a custom configuration. For this demo we will choose “Cost Effective DR”.
8. Provide the name of the volume and its size. For this demo, we will select NFS as the protocol and use the default export policy shown in the wizard. Click on “Continue”: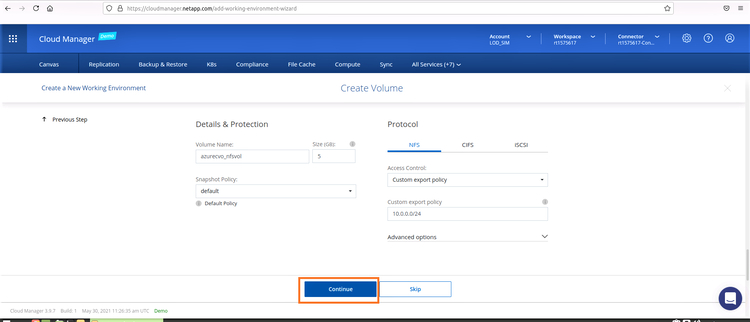
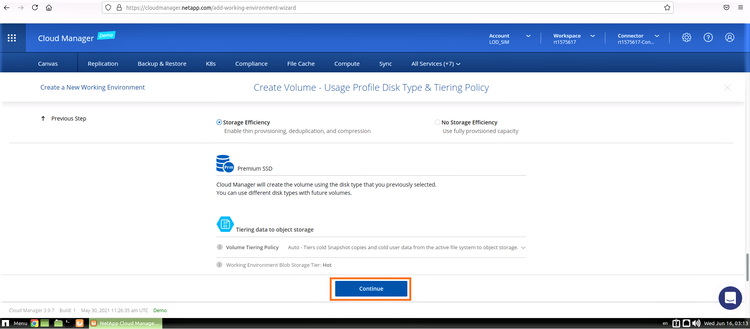
9. Use the default storage efficiency options and click “Continue”:
10. Accept the two agreements in the next screen regarding activating support and allocation of Azure resources. Click on “Go” to create the Cloud Volumes ONTAP instance: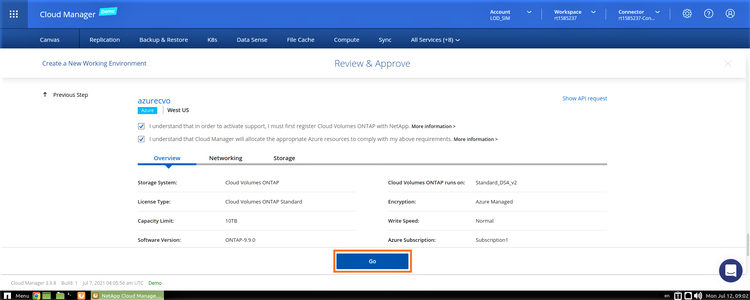
11. Once provisioned, Cloud Volumes ONTAP will be listed in the working environments along with your other ONTAP systems in the Canvas page.
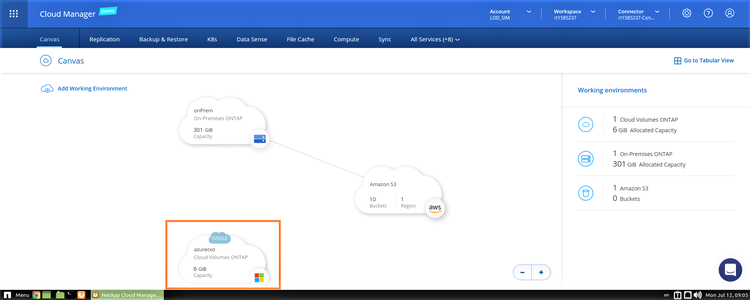
Create a Replication Relationship
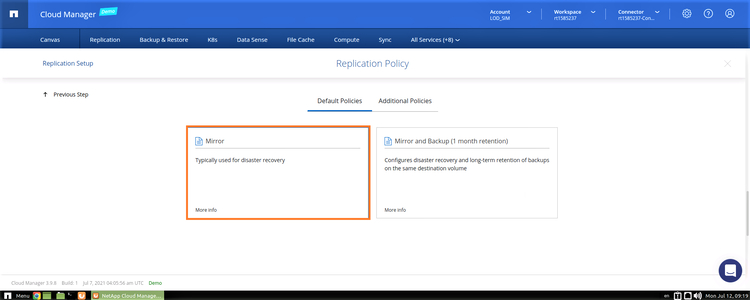
Snapshots are created automatically by ONTAP operating systems as a default backup mechanism. To configure replication between different source and destination ONTAP environments, the user should configure the data replication policies that specify how snapshots will be copied over to the destination volume. The following replication policies are available:
- Mirror Policy: Copies the newly created snapshots to the destination. This is suitable in DR scenarios, where the destination volume can be activated at any time for data access.
- Backup Policy: This policy is used for copying specific snapshot copies to the destination volume, mainly for backup and long-term retention purposes, allowing you to restore to different points in time.
- Mirror and Backup Policy: As the name indicates, this option combines both Mirror and Backup policies and is useful for DR as well as long-term retention.
These policies are included in the system. Alternatively, you can create custom policies of your own.
1. From the Canvas page, you will be able to see your main working environments. Drag and drop the source on-prem environment to the target Azure environment.
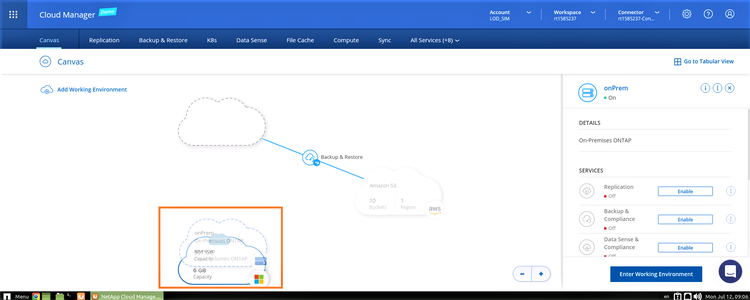
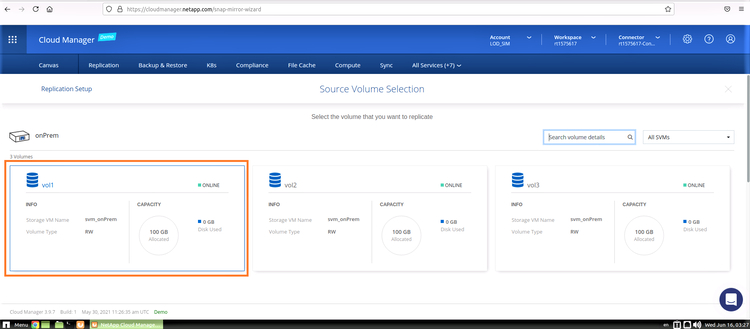
2. Select the volume to be replicated, as shown below:
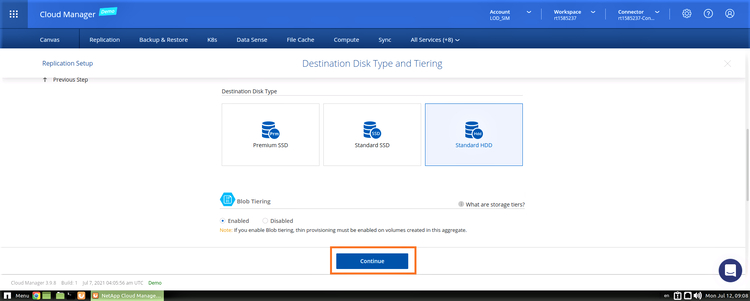
3. Use the default selection of Standard HDD as your disk type and enable Blob tiering for volumes created with thin provisioning. Click “Continue”:
4. Provide a name for the destination volume or use the default name provided. Click “Continue” to proceed to the next step.
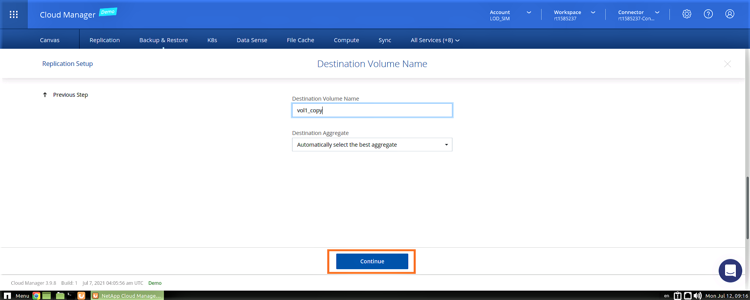
5. Configure the transfer rate and set a limit so that it does not impact application performance or adversely affect the network bandwidth. Click “Continue” to proceed:
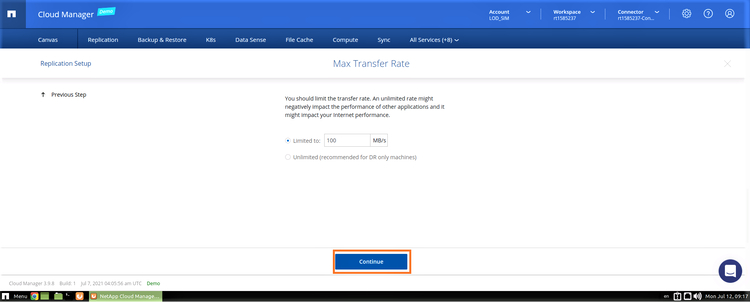
6. In this step, choose the replication policy. For this scenario, we will choose the Mirror policy which is sufficient for the purposes of disaster recovery.
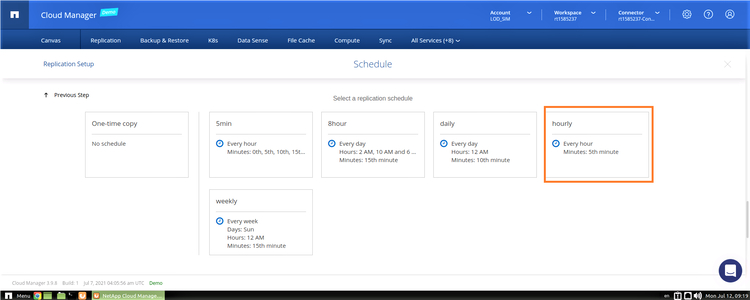
7. In the “Schedule” window, choose a replication schedule based on the available options listed. This will define the data recovery point objective (RPO) of your DR solution. For this scenario, we will be using the “hourly” replication schedule.
8. Review the configuration, tick the "I understand..." box to approve, and click on "GO" to start the replication process:
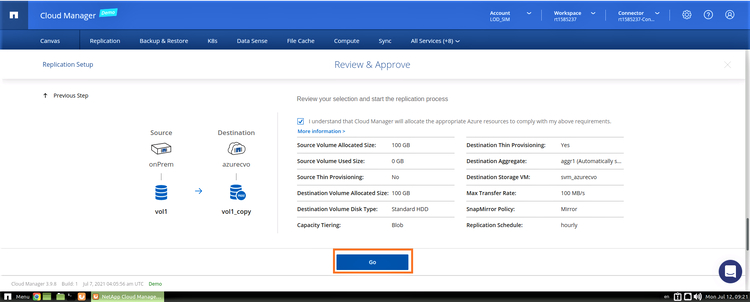
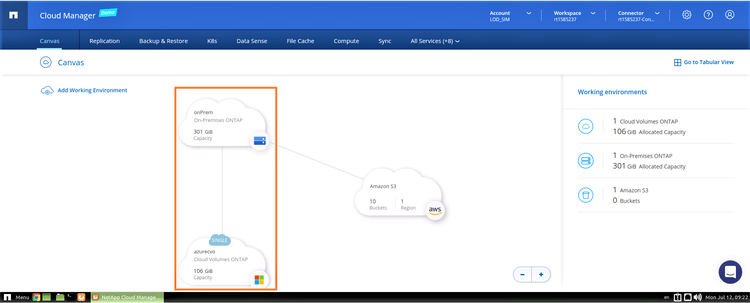
9. Once the replication is completed successfully, you can see the replication relationship in the working environments view on the Canvas tab.
As you can see in the screenshot below, the on-prem volume is now being replicated to Cloud Volumes ONTAP in Azure:
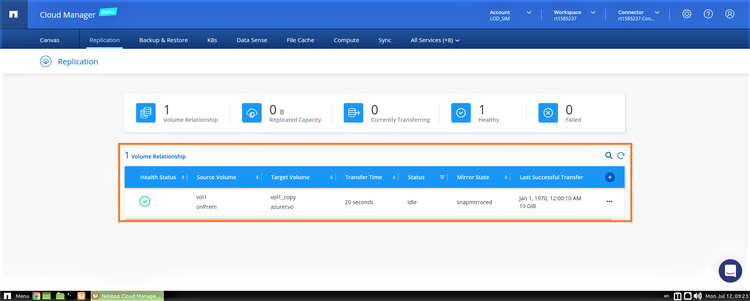
Monitor and Manage the Replication Relationship
1. You can view the status of replication in the “Replication” tab of BlueXP Console. This view will show the source and target volumes, the relationship status, last copy, etc.
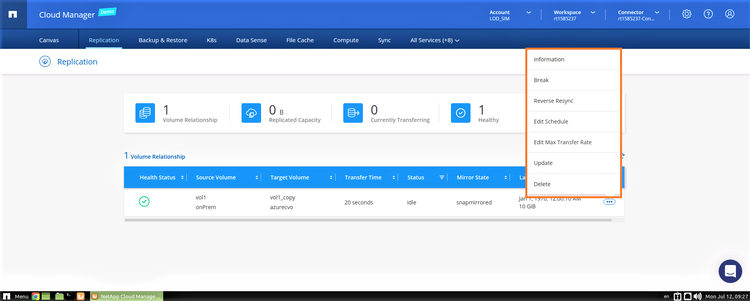
2. You can also manage replication configuration from the same view. Click the ellipses button (the three dots) to the right of the relationship line to view the various options.
For example, you can break the replication, reverse sync the data (used during a failback operation), edit the sync schedule, and more.
Conclusion
Cloud Volumes ONTAP offers a cloud-based disaster recovery solution for your storage. The solution can be configured for Azure as well as for AWS disaster recovery, and it can operate alongside an Azure Site Recovery architecture to augment your disaster recovery strategy in Azure. It offers better protection and security when compared to traditional disaster recovery solutions and caters to multicloud and hybrid cloud architectures for enterprises.
.png?width=75&height=75&name=yuval-on%20demand%20(1).png)