More about Infrastructure as Code AWS
Subscribe to our blog
Thanks for subscribing to the blog.
December 24, 2019
Topics: Cloud Volumes ONTAP DevOpsAWSAdvanced7 minute readAutomation
Infrastructure as Code solves an age-old problem: setting up and configuration IT resources was an arduous, manual, error-prone process. Today it is possible to define a configuration file, and spin up IT resources automatically, consistently and predictably, from that file. This can be extremely useful for DevOps processes, workload management, and other cloud automation use cases.
Infrastructure as Code strategies on AWS are powered by the CloudFormation service, which lets you define simple text-based templates, and use them to spin up surprisingly complex cloud architectures.
CloudFormation uses templates, configuration files defined in JSON or YAML syntax, that are human readable and can be easily edited, which you can use to define the resources you want to set up. CloudFormation reads a template and generates a stack, a set of resources ready to use on AWS.
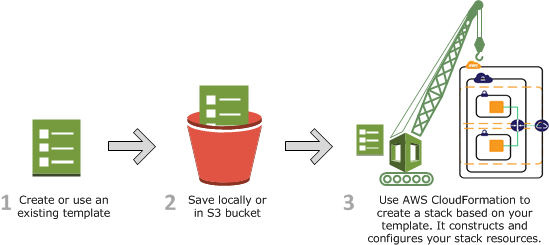
Image Source: AWS
By using CloudFormation, you can define complex multi-resource applications and automatically deploy the resources on AWS. You can test your Infrastructure as Code by fine-tuning your configuration and repeating the process.
In this article, you will learn:
- Benefits of IaC on AWS
- AWS CloudFormation: Basics of Infrastructure as Code on AWS
- 5 Tips for Building IaC on Amazon with CloudFormation
- Infrastructure as Code on AWS with Cloud Volumes ONTAP
Benefits of IaC on AWS
The AWS approach to Infrastructure as Code has several advantages:
- High visibility—CloudFormation templates are just code—they can be viewed and edited with any text editor. They clearly state which resources will be created and defines their parameters, making it easy for everyone on your team to see and understand what is being deployed.
- Automated deployment and orchestration—CloudFormation takes a declarative approach, allowing you to declare the end result of your deployment, and performing the right set of operations to get you there. Even if you specify a complex multi-part application, there is no need for scripting or manual actions—CloudFormation can create a working stack fully automatically.
- Stability with version control—changes to templates can create unintended consequences, errors or service interruption. You can save your CloudFormation templates in a version control system, maintain a tested production version of your template, and if anything goes wrong, tear down the resources and revert to the tested, working template. CloudFormation also tests that a deployment was successful and if it detects errors, it rolls back gracefully to a last known good configuration.
- Reusability and scalability—AWS lets you deploy the same template as many times as you need. You can define and test a stack one time and then reuse it for many systems across your enterprise, or to scale up the same system by deploying it several times. This is also useful for AWS migration efforts—when migrating services to the cloud, it is often useful to start them up using CloudFormation templates.
AWS CloudFormation: Basics of Infrastructure as Code on AWS
CloudFormation allows you to define configuration for Infrastructure as Code, by directly editing template files, via the CloudFormation API, or the AWS CLI. CloudFormation is a free service—Amazon only charges for the services you provision via templates.
The following diagram illustrates the CloudFormation process. You create templates and save them in an S3 bucket. Then CloudFormation reads the template and creates a stack based on template definitions.
Managing template changes
What happens when you need to change a template? CloudFormation recognizes that a template has been edited and creates a change set, which specifies what needs to be changed in the resources you have provisioned, to reflect the changes in the template. Once you approve the change set, it is executed, and the resources are automatically modified.

CloudFormation template example
Here is an example of a sample CloudFormation template provided by Amazon, which creates a publicly accessible Amazon S3 bucket, with external access, and a “retain on delete” deletion policy.
This is the JSON syntax—you can also define templates using YAML.{
"AWSTemplateFormatVersion" : "2010-09-09",
"Description" : "AWS CloudFormation Sample Template
S3_Website_Bucket_With_Retain_On_Delete",
"Resources" : {
"S3Bucket" : {
"Type" : "AWS::S3::Bucket",
"Properties" : {
"AccessControl" : "PublicRead",
"WebsiteConfiguration" : {
"IndexDocument" : "index.html",
"ErrorDocument" : "error.html"
}
},
"DeletionPolicy" : "Retain"
}
},
"Outputs" : {
"WebsiteURL" : {
"Value" : { "Fn::GetAtt" : [ "S3Bucket", "WebsiteURL" ] },
"Description" : "URL for website hosted on S3"
},
"S3BucketSecureURL" : {
"Value" : { "Fn::Join" : [ "", [ "https://", { "Fn::GetAtt" : [ "S3Bucket", "DomainName" ] } ] ] },
"Description" : "Name of S3 bucket to hold website content"
}
}
}
5 Tips for Building IaC on Amazon with CloudFormation
1. Use IAM to Control AccessAmazon Identity and Access Management (IAM) manages users and permissions in AWS. You’ll need to use IAM in conjunction with CloudFormation to define which operations CloudFormation is permitted to carry out. Before a user can deploy a stack with CloudFormation, that user should have permissions to all the relevant resources in the stack—for example, permission to create instances on EC2, or to create new S3 buckets.
You can use a service role to avoid tying CloudFormation capabilities to the permissions of a specific user. You can define one or more service roles for CloudFormation, giving those roles permission to create, modify, and delete resources. Prefer a granular permission policy with several service roles for different types of stacks, rather than one “super admin” role that can represent a major security risk.
2. Verify account limits and budget for relevant resource types
Check your AWS account limits for the resources that participate in your stack, and whether the limits prevent you from launching any part of the stack. There are also specific limits related to CloudFormation—you can launch only 200 CloudFormation stacks per region by default. If you defined budgets for your AWS account, you should also verify that the resources created by your stack do not exceed the budget for the relevant AWS account.
3. Reuse templates to replicate your stacksOnce you have built a template and tested to ensure it works well, reuse it to rebuild that infrastructure in other environments. For example, if you set up a working stack for your web application, you can reuse it to create dev, test, and production environments that all have the same components. When creating your template, keep in mind that the template should be reusable, and use parameters and conditions to generalize the template beyond the current, specific deployment scenario.
4. Use nested stacksA nested stack is a CloudFormation template that references another template, to reuse the same stack within another stack. You can use CloudFormation to create a set of “lego blocks” from which to assemble your infrastructure.
For example, you can have a template for a load balancer configuration, a template for setting up an S3 bucket, and another for spinning up certain types of EC2 instances. Instead of explicitly declaring these resources in your templates, use your tested “lego block” templates. This also means you can maintain and update basic templates and apply the change to your entire infrastructure at once.
5. Validate and test your templates before useCloudFormation provides a validation engine that scans a template and helps you catch syntax and semantic errors. If your template passes validation, always run it in an isolated non-production environment and test it to ensure resources are running correctly, and there are no performance or security issues. When you reach a stable state, commit your template into source code, labelling it as a stable, tested version.
Infrastructure as Code on AWS with Cloud Volumes ONTAP
NetApp Cloud Volumes ONTAP, the leading enterprise-grade storage management solution, delivers secure, proven storage management services on AWS, Azure and Google Cloud. Cloud Volumes ONTAP supports up to a capacity of 368TB, and supports various use cases such as file services, databases, DevOps or any other enterprise workload.
In particular, Cloud Volumes ONTAP provides Cloud Manager, a UI and APIs for management, automation and orchestration, supporting hybrid & multi-cloud architectures, and letting you treat pools of storage as one more element in your Infrastructure as Code AWS setup.
Cloud Manager is completely API driven and is highly geared towards automating cloud operations. Cloud Volumes ONTAP and Cloud Manager deployment through infrastructure- as- code automation helps to address the DevOps challenges faced by organizations when it comes to configuring enterprise cloud storage solutions. When implementing infrastructure as code, Cloud Volumes ONTAP and Cloud Manager go hand in hand with Terraform to achieve the level of efficiency expected in large scale cloud storage deployments.
Ansible is a powerful tool for automating the deployment of cloud resources. When integrated with AWS, it can help you manage your applications and services consistently and with ease.
Learn More About Infrastructure as Code on AWS
Ansible & AWS: How to Automate Anything in AWS with Ansible Modules
Ansible is a powerful tool for automating the deployment of cloud resources. When integrated with AWS, it can help you manage your applications and services consistently and with ease.
This article explains how Ansible can improve your AWS management, how the two work together, and how to get started with Ansible playbooks for automation.
Read more: Ansible & AWS: How to Automate Anything in AWS with Ansible Modules
Terraform for EBS and EFS: Automating EBS Volumes and EFS File Shares with IaC
Terraform is an infrastructure as code (IaC) solution you can use to define and manage your resources in AWS. You can use it with a variety of services, including both EBS and EFS, to automate provisioning and improve efficiency.
This article explains the basics of how Terraform can combine with AWS, what AWS data sources are available, and provides two brief tutorials showing how to create resources in EBS and EFS.
Read more: Terraform for EBS and EFS: Automating EBS Volumes and EFS File Shares with IaC
Terraform & AWS Tutorial: How to Deploy a Terraform Enterprise Cluster on AWS
Terraform is an infrastructure as code (IaC) tool that you can use to define, version, and manage your infrastructure. Terraform works on-premises or in the cloud, including with AWS, making it a valuable tool for flexible deployments.
This article explains how Terraform can simplify resource deployment in AWS, how to deploy an enterprise grade cluster, and provides some tips for getting the most out of management with Terraform.
Read more: Terraform & AWS Tutorial: How to Deploy a Terraform Enterprise Cluster on AWS
See Additional Guides on Key DevOps Topics
Together with our content partners, we have authored in-depth guides on several other topics that can also be useful as you explore the world of DevOps.
GitOps
Authored by Codefresh
- What is GitOps? How Git Can Make DevOps Even Better
- GitOps vs. DevOps: How GitOps Makes DevOps Better
- GitOps with Kubernetes: Why It’s Different and How to Adopt It
Cloud Optimization
Authored by Granulate
- AWS Optimization: The Basics and 15 Ways to Optimize Your Cloud
- Cloud Optimization Best Practices for AWS, Azure, and GCP
- EC2 Auto Scaling: How It Works, Examples, and Key Challenges
kubectl Cheat Sheet
Authored by Komodor
- The Ultimate Kubectl Command Line Cheat Sheet
- kubectl config Explained: How to Configure Cluster Access
- kubectl apply: Syntax, Examples, and kubectl apply vs. create vs. replace
