More about NetApp Ransomware Protection
- What Should Your Data-Centric Ransomware Protection Include?
- Anti-Ransomware: Why Backup and Perimeter Protection Aren’t Enough
- The Zero Trust Model: What It Is and How It Affects Data Management
- Ransomware Protection Services and Solutions: A Market Overview
- IT & Ransomware: IT’s Role at the Forefront of Ransomware Protection
- Ransomware Detection: Techniques and Best Practices
- Data Security Capabilities Every IT Leader Needs To Know
- Ransomware Protection: Detection, Recovery, and Prevention
- Organization Security: Who’s Responsible for Keeping IT Safe?
- Ransomware Types: 5 Common Types of Ransomware Attack Top Security Tips for IT Teams
- Cyberstorage: Data-Oriented Security Designed for Ransomware Protection
- NetApp Ransomware Protection: A Complete Set of Data-Focused Protective Capabilities
- Ransomware Prevention and Remediation with Cloud Volumes ONTAP
Subscribe to our blog
Thanks for subscribing to the blog.
August 31, 2022
Topics: Data ProtectionAdvanced8 minute readRansomware ProtectionSecurity
No matter how many security precautions you take, your data is always at risk from falling victim to ransomware attacks. The simple reality that many organizations have to face is that the attackers will always find a way through the perimeter defenses.
The new thinking by security experts is that the only hope of protecting data lies in designing systems that put data first, instead of focusing on protecting the network. What do such data-centric systems look like?
In this blog we’ll dive into the defining characteristics of a data-centric approach to ransomware protection and see how it resembles safety systems that many people take for granted every time they get in a car and turn onto the road.
Read on or use the links below to jump down to:
- The Five Functions of Cyber Resilience
- How the Data Centric Approach Is Built from the Inside Out
- The Levels of Data-Centric Protection
- NetApp Knows Data—And How to Protect It
- Ready to Hit the Road? Better Buckle Up
The Five Functions of Cyber Resilience
A core part of understanding a data-centric security posture is to consider how cyber resilient systems are built.
As defined by the National Institute for Standards and Technology (NIST) in Ransomware Risk Management: A Cybersecurity Framework Profile, cyber-resilient systems have five functions to include in the framework:
- Identify: This function helps manage risks to systems by properly taking stock of the data, the systems where the data resides, and its capabilities.
- Protect: The line in the sand to stop intruders from gaining access to data.
- Detect: Being able to correctly determine when a cyberattack is taking place before the damage is done.
- Respond: When attacks do take place, this function ensures that the system has the ability to take corrective action.
- Recover: It’s essential to have the plans and capabilities in place to return systems to a functional state after attacks take place.
While these goals for cyber resilience aren’t specific to ransomware, when they are applied in a data-centric context they can significantly increase the security posture of the organization against ransomware. That’s because ransomware’s main goal is to take over and corrupt your data.
How the Data Centric Approach Is Built from the Inside Out
In a data-centric context, cyber resilience is centered on the state of the data itself, with the overall system’s wellbeing built out from there.
By focusing on data first, the data is more likely to survive a cyber event. Consider how cars are designed. The most important safety features that cars have—airbags, seat belts, crush zones, car seat attach points, rollover strength, side impact protection—are all designed with one thing in mind: keep the people inside the car safe. Some features, like proximity sensors, are there to make sure those features never need to be utilized, but no one is getting into a car and just relying on proximity sensors. People are the main focus of the most important safety features because people are more important than making sure the exterior, the engine, or the wheels survive an impact.
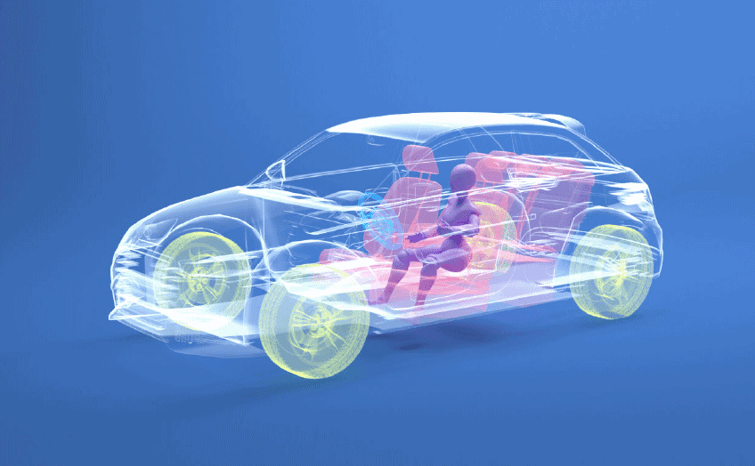
Data-centric cyber resilience is designed the same way—with your data at the center.
The Levels of Data-Centric Protection
As data-centric approach begins with data at the center, it starts from the innermost levels of data protection and moves on to the outer levels. In this section we’ll take a look at each of these levels, working from the inside out, showing how NetApp Ransomware Protection capabilities can help.

1. Data content
At the very core of your protection strategy lies your data. Understanding the data you have and how it should be protected are the keys to defend against ransomware.
Using AI-driven data governance capabilities of NetApp’s Cloud Data Sense, you can map, classify, and segment all of the data across your data estate. With this information, you can continuously make the right adjustments to properly secure your data and mitigate the risks involved with ransomware.
-1.gif?width=755&name=ezgif.com-gif-maker%20(2)-1.gif)
Cloud Data Sense, AI-driven data governance capabilities
2. Metadata
Metadata contains all the attributes about your data, and it can play a key role in its defense. These attributes define who can access your data and provide protection mechanisms with the ability to block storage operations such as the modification, deletion, and creation of files.
Using your metadata, NetApp’s capabilities give you the ability to analyze file access permissions so you can get insights into file and folder level permissions, and block malicious files from being created using NetApp FPolicy.
3. Data usage
After establishing what data you have and who can access it, comes how it’s used. Continuously analyzing the behavior of how users and systems use the data is the best way to stay one step ahead and protectively detect when something is not right.
NetApp has a range of capabilities that address how data is used. Storage anomaly detection is possible through machine-learning analysis that continuously scans your workloads so you can identify, prevent, and limit sophisticated ransomware attacks. User anomaly detection through NetApp's UBA capability helps determine if something is unusual about how data is being used, so access can automatically be cut off.
4. Data storage
The capabilities of your storage system are key to understand how you can respond and recover when ransomware is detected. Advanced solutions will provide more options and even enable an automated response that can ensure business continuity.
NetApp knows storage better than anyone, so it’s no surprise that it offers a wide range of anti-ransomware capabilities at the storage layer, including:
- Immutable data copies with read-only NetApp Snapshot copies that can be the basis of system restores.
- Secure backup methods such as those provided by NetApp Cloud Backup’s incremental forever, block-level back up methods.
NetApp’s Cloud Backup
- Efficient data replication to a different geographic location or backup site.
- Air-gapped copies can prevent bad actors and ransomware from accessing your backups via NetApp's data locking capability, without any need for physical separation.
- Role-Based Access Control (RBAC) gives users the ability to decide who gets access to specific storage systems and what actions they can perform.
- Multi-factor authentication (MFA) plays a key role in stopping or slowing a ransomware attack by requiring additional access information to target accounts and triggering alerts.
- Active Directory monitoring constantly monitors your active directory to find anomalous activities or unnecessary privilege allocations that might be exploited.
5. Cyber resilience best practices and recommendations
This is an important part of your ransomware protection journey. Understanding and adopting industry-approved best practices provides you with a holistic understanding on all of the levels that need to be covered in your protection strategy.
NetApp can help you do this with a number of features. Ransomware early detection comes through built-in tools that help detect ransomware before major damage can be done, such as Active IQ Unified Manager and Active IQ digital advisor.
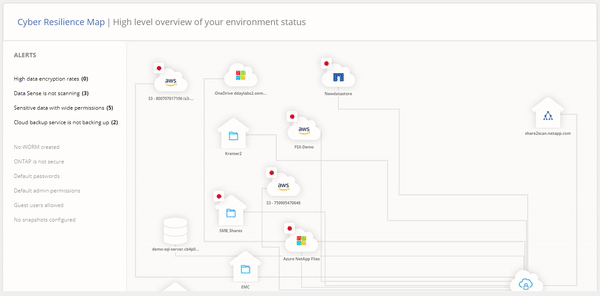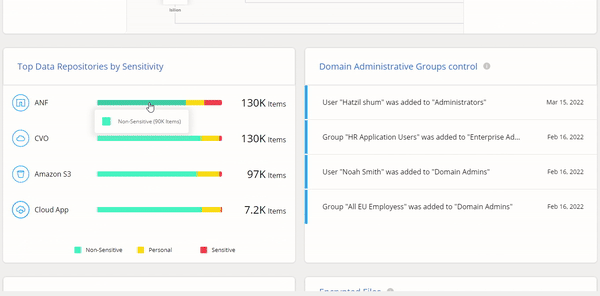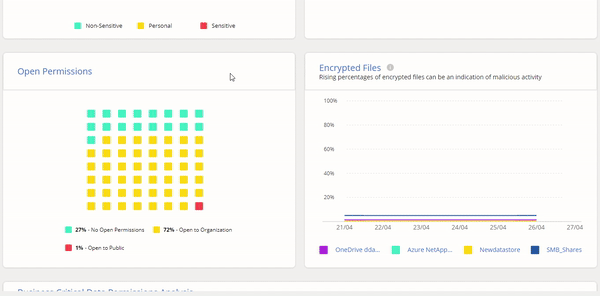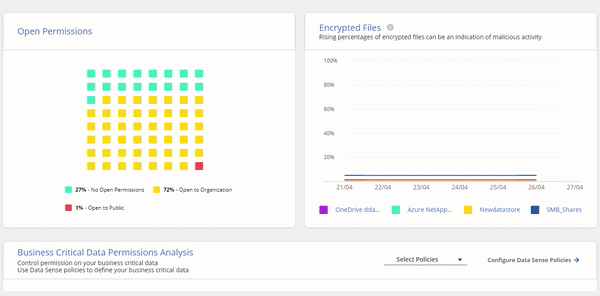
Cloud Manager’s Ransomware Protection Dashboard is dedicated to letting you respond to threats in real time. This feature gives IT teams an overview that helps them manage their entire cyber resiliency posture with visibility of the entire on-prem and cloud data estate.
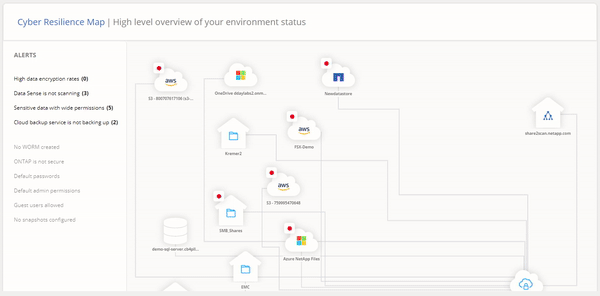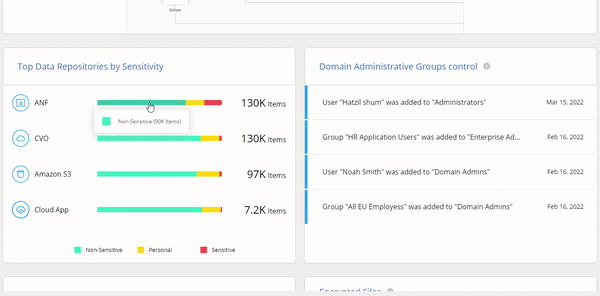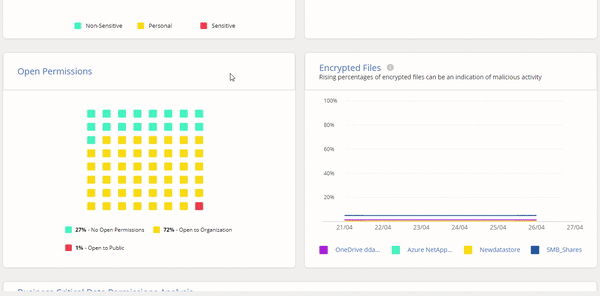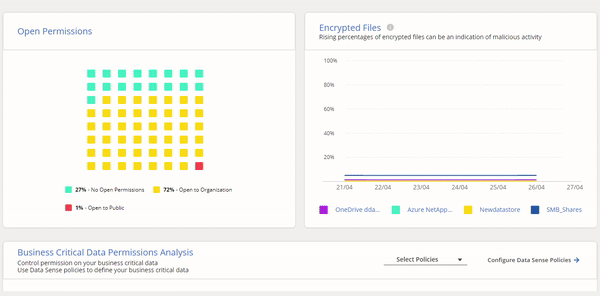
Cloud Manager’s Ransomware Protection Dashboard

NetApp Knows Data—And How to Protect It
There’s a vast amount of capabilities with technological complexities for adopting a data-centric approach. While this approach brings your security posture to a whole new level, it’s important to complement them with traditional security mechanisms.
After all the inner levels of data are protected, the network perimeter capabilities enter the picture. Typical mechanisms such as firewalls and anti-viruses are examples of external level security that should be implemented on top of data-centric layers.
As a pillar of the storage service industry, NetApp knows data, from how it’s stored to how it’s used. That knowledge is why NetApp is able to provide users with protection from ransomware at the data-level, safeguarding not just the secondary backup copies you rely on as a failsafe, but the vital production data that fuels your day-to-day operations.
NetApp’s Ransomware Protection offerings collect all of these capabilities in one place, following the zero-trust design principles known as cyberstorage. That means data is provided with a full complement of cyber-resilient features—from data monitoring that can alert you about abnormal activity and controls for managing user access to automatic back up processes and the fastest restores possible—so you have the strongest security posture possible. This goes beyond the usual industry practices, which either protect the network or simply rely on backups.
Ready to Hit the Road? Better Buckle Up
Just like a driver takes a chance every time they pull out into the road, enterprise IT departments need to realize that there is always a risk to their data. Making sure that it stays safe is a matter of building up the same kind of security design that tries to make sure that driver stays safe, no matter what happens.
NetApp Ransomware Protection capabilities give you the assurance so that when ransomware and other cyber-attacks take place, your data will be as secure as possible.

