More about NetApp Ransomware Protection
- What Should Your Data-Centric Ransomware Protection Include?
- Anti-Ransomware: Why Backup and Perimeter Protection Aren’t Enough
- The Zero Trust Model: What It Is and How It Affects Data Management
- Ransomware Protection Services and Solutions: A Market Overview
- IT & Ransomware: IT’s Role at the Forefront of Ransomware Protection
- Ransomware Detection: Techniques and Best Practices
- Data Security Capabilities Every IT Leader Needs To Know
- Ransomware Protection: Detection, Recovery, and Prevention
- Organization Security: Who’s Responsible for Keeping IT Safe?
- Ransomware Types: 5 Common Types of Ransomware Attack Top Security Tips for IT Teams
- Cyberstorage: Data-Oriented Security Designed for Ransomware Protection
- NetApp Ransomware Protection: A Complete Set of Data-Focused Protective Capabilities
- Ransomware Prevention and Remediation with Cloud Volumes ONTAP
Subscribe to our blog
Thanks for subscribing to the blog.
May 29, 2022
Topics: Data ProtectionAdvanced9 minute readRansomware ProtectionSecurity
Ransomware is the number one cybersecurity concern for any enterprise. It can have a crippling impact on your business—from loss of data and productivity to costly recovery processes and damage to your reputation. In this light, knowing what kind of ransomware you’re dealing with can be crucial to your ransomware protection plans.
There has been a proliferation of ransomware kits on the dark web, and criminals can launch an attack with relatively little effort or technical knowledge. So what can you do to protect your valuable data assets?
In this post, we will take a look at the major ransomware types in use today, some of the largest ransomware attacks that have taken place to date and show you how NetApp can help you better protect your data where it resides—the storage layer.
Use the links below to jump down to these sections:
- The 5 Ransomware Types
- How Do the Hackers Get In?
- The Biggest Ransomware Threats to Date
- Security Tips for Storage Administrators
- The Solution: Data-Centric Ransomware Protection
- FAQs
The 5 Ransomware Types
Ransomware comes in a number of different forms, all of which share several common characteristics.
First of all, they're all financially motivated. Second, they each carry some form of threat in relation to the victim's IT system. Third, they all send or display a message demanding a ransom—where payment is required, usually by Bitcoin or some other cryptocurrency.
But what distinguishes different ransomware from each other is the specific attack techniques they use. Let’s take a look at each of these attack methods to see exactly what kind of threats they pose.
1. Crypto Ransomware
Risk level: High
Crypto ransomware, which is also known as data kidnapping, is both an effective and highly lucrative method of attack. This makes it a popular choice amongst cybercriminals and therefore one of the most common forms of ransomware.
In such an attack, the perpetrator encrypts your data so it's unreadable and then demands a ransom in exchange for the keys to decrypt it. In addition, the attacker will often attempt to encrypt your backups to prevent you from performing a data restore.
2. Exfiltration (Leakware)
Risk level: High
Exfiltration, which is also known as doxware or leakware, is where a malicious actor steals sensitive data and threatens to release it into the public domain.
This can have potentially severe consequences for both your business and the individuals affected. It can be particularly damaging for your company's reputation. It could also potentially lead to a substantial fine for breach of data protection regulations.
Attackers often carry out data theft and encryption in conjunction with each other. That way, they can increase the pressure to pay the ransom.
3. DDoS Ransomware
Risk level: Moderate
Unlike crypto ransomware and exfiltration, distributed denial-of-service (DDoS) ransomware attacks target your network services, not your data.
They work by flooding your servers with spurious connection requests in a bid to bring them to a standstill. This is accompanied by a ransom note, telling you the attack will end once payment is made. However, a malicious party will sometimes send the ransom note first and may or may not follow through with the threat if their demands aren't met.
A DDoS ransomware attack is highly resource intensive. So a hacker may struggle to sustain it for any extended period. Furthermore, DDoS ransomware doesn't pose a threat to your actual data.
4. Screen Lockers (Locker Ransomware)
Risk level: Low
A screen locker is a common type of malware that prevents you from accessing a computer or device until you meet the attacker's ransom demands.
When you try to power up or log into an infected machine, the screen locker displays a message calling for payment. This is often accompanied by a countdown timer designed to scare the victim into paying before the ransom increases or they purportedly lose their files.
It's generally easier to recover from screen-locking attacks, as they don't encrypt your data. For example, it's often possible to remove the malware from a machine by rebooting it in safe mode and running antivirus software.
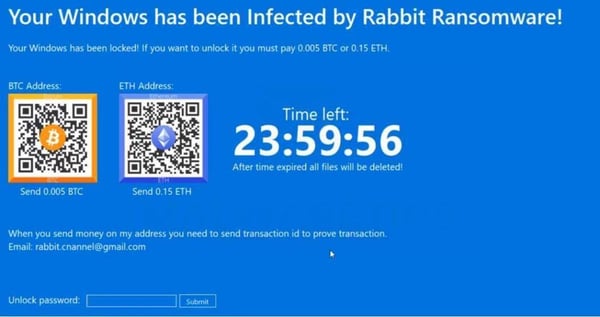 Rabbit Ransomware, which locks infected Windows machines. Source: MalwareTips.com
Rabbit Ransomware, which locks infected Windows machines. Source: MalwareTips.com
5. Scareware
Risk level: Very low
Scareware employs social engineering tactics to trick the user into believing their computer has been infected with malware or has run into some other kind of problem that requires urgent action.
It displays a pop-up alert, which often shows the logo of legitimate security software, instructing you to purchase and install software to resolve the issue.
The software may do nothing more than remove the message or it may contain malware designed to cause more serious harm.
How Do the Hackers Get In?
With all of these ransomware types, the techniques cybercriminals use to initiate an attack are much like those used to spread other forms of malware. These include:
- Phishing emails with malicious links or attachments
- Compromised websites and peer-to-peer file sharing networks
- Exploitation of security vulnerabilities
- USB flash drives
The Biggest Ransomware Threats to Date
Here are some of the ransomware types that have caused the most damage, past and present.
WannaCry
WannaCry is encrypting ransomware. It exploits a vulnerability in the Windows SMB protocol. WannaCry can self-propagate, allowing it to infect other machines.
Marketed as a dropper, WannaCry is a self-contained program. This program can extract files containing encryption keys, encryption/decryption applications, and the Tor communication program. Attackers do not obfuscate WannaCry, so you can relatively simply identify and remove it.
In 2017 it affected 230,00 computers spreading across 150 countries. It caused an estimated $4 billion worth of damages.
Cerber
Cerber is ransomware-as-a-service (RaaS). Cybercriminals can use this when executing attacks and spreading their valuable information with the malware developer.
Cerber runs undetected while encrypting files and attempts to stop antivirus and Windows security features from running. This approach may prevent users from restoring their system. When it effectively encrypts files on the machine, it presents a ransom note on the desktop background.
CryptoLocker
Ransomware has existed in different forms for the past two decades. In 2013, with CryptoLocker, it gained stature. Vendors and IT specialists eradicated the original CryptoLocker botnet in May 2014 after the cybercriminals extorted close to $3 million from victims.
Cybercriminals readily copy the CryptoLocker approach. The variations used today don't correlate directly to the original version. The world CryptoLocker has become synonymous with ransomware.
Locky
Locky ransomware employed the Necurs botnet to distribute phishing emails containing malicious instructions via Excel or Word attachments. Locky encrypted files on Windows OSes.
A June 2016 version detected if malware was running in a sandbox. A July 2016 variant was capable of encrypting files offline. Locky became active again in September 2017 in an attack that saw 23 million phishing messages sent out by attackers in 24-hours.
Maze ransomware
Maze ransomware was discovered in 2019. It came to prominence for being responsible for releasing information belonging to targets, primarily from the healthcare sector. The Xerox Corporation was also one of the recent victims of the Maze ransomware attackers, who stole over 100 GB of files.
Petya and NotPetya
Petya is ransomware that operates at the operating system level, and only impacts Windows systems. It requires permission from the user to gain admin-level access, and then reboots the computer and shows a fake crash screen, while encrypting the entire Master File Table (MFT) in the background.
Based on the original Patyal virus, attackers created NotPetya, which was much more dangerous because of its unique ability to spread itself. NotPetya exploited vulnerabilities in the Windows SMB file transfer protocol, known as EternalBlue and EternalRomance to infect any Windows machine connected to the originally infected device. Another feature of NotPetya is that it encrypts entire hard disks in a way that they cannot be recovered, even if the victim pays the ransom.
Ryuk
Ryuk is ransomware that is distributed via a dropper application, which is deployed on a victim’s machine and then installs a trojan and establishes a persistent connection with a command and control (C&C) server.
Ryuk is commonly used as part of advanced persistent threat (APT) campaigns, and can install additional tools to record user activities, perform privilege escalation, and exfiltrate data. One of these tools is locker ransomware that locks down the machine and encrypts files in the background—this is the final stage of a Ryuk attack, after attackers have compromised the environment and stolen valuable data.
Security Tips for Storage Administrators
To combat the threats of any of these ransomware types, the section below will give you the most important data-oriented measures storage teams can take to protect your business from high-risk ransomware attacks, such as data kidnapping and exfiltration.
Identify and Remediate Insecure File Permissions
You need to understand your data in order to properly protect it. In particular, you need to know what types of data your organization stores and who has access to it.
The best place to start is analyzing file permissions. Analyzing file permissions lets you see what different users are able to do with your data and then tighten up those permissions that aren't actually necessary.
Similarly, you should look for any misuse of permissions by users who are reading, changing, or deleting data that they're not normally meant to as part of their role. For example, this could be a rogue application developer, who has been changing information on the live system.
However, insight into file permissions won’t be complete unless you understand the nature of the data being accessed. So you'll need tools that can enrich your file permission analysis with contextual information, such as different categories of data type, sensitivity, ownership, and storage location.
Log and Monitor Data Usage Patterns
In addition, you should log all user activity on your files for monitoring and analysis.
This will be invaluable in the event of a breach, as your logs will provide the information you need to assess the impact of the attack and take appropriate remedial action.
They will also provide forensic details to help you establish the root cause of the attack and implement future preventative measures.
Potential signs of a ransomware offensive include:
- Mass read, write, or delete activity
- Abnormal increases in encryption
- User access outside normal working hours
- Access from an unexpected device or geolocation
You should not only monitor user activity but also system behavior. This can help you spot other signals of an attack, such as unusual system stress or loss in storage efficiency.
Encrypt Data at Rest and in Flight
Data encryption is the best way to prevent exfiltration, as it renders the data useless to attackers unless they can gain access to your cryptographic keys. But bear in mind your backup data is just as useful to cybercriminals. So you'll also need to encrypt your data at rest in your backup environment and in transit during the backup process.
Following key management best practices can also help prevent your keys from falling into the wrong hands.
Finally, be aware that encryption cannot stop crypto ransomware, as bad actors can simply encrypt the encrypted form of your data. That would mean you'd then need both your and the attacker's keys in order to decrypt it.
Back Up Your Data
It should go without saying you should have a backup strategy in place to ensure you're sufficiently covered in the event of a crypto attack. This should follow the 3-2-1 backup principle. In other words, you should:
- Store at least three copies of your data—your live data and at least two backups
- Use at least two different types of storage medium—to minimize the risk of failure
- Back up your data to at least one an offsite location—so it's effectively air-gapped from your live system
For the best possible protection against ransomware, you should also take immutable backups. These cannot be modified, encrypted, or deleted by anyone until the end of a specified locking period—not even by users with admin privileges.
You also need to be sure your backups actually work if ever you need to restore them. So don't forget to test them on a regular basis.
The Solution: Data-Centric Ransomware Protection
IT teams rely on a whole host of network, endpoint, and access control measures to help keep unwanted hands away from your data. But it's still not enough to combat new and more sophisticated forms of ransomware.
However, cyberstorage is an emerging technology that offers a data-oriented solution for today's data-oriented security problems. It is a unified set of capabilities that enterprise storage has always needed, providing an inside-out approach to protect organizational data. NetApp provides such a view with the new NetApp Ransomware Protection dashboard.
Ransomware Protection gives you the ability to map your data, get insights such as the permission and encryption status of your files, alerts to signals of malicious activity, remediation recommendations, and a full range of backup and recovery features to help you restore your data in the event of an attack. It also provides full visibility across your entire data estate through a single pane of glass.
Storage wasn't originally designed with security in mind and has always been the most vulnerable component of enterprise IT infrastructure. But cyberstorage via NetApp’s set of capabilities seeks to address these longstanding security shortcomings.
And the good news is that it doesn't come with any additional performance overhead compared with traditional storage solutions.

FAQs
What is the most common type of ransomware?
The most common type of ransomware attack is crypto ransomware. This type of ransomware attack is leveraged by cybercriminals because of its effectiveness in locking users out of the data and systems.
With crypto ransomware, malicious code encrypts a part or all of a user’s data, locking out users and making the system useless until the ransom is paid and the decryption keys handed over. It’s clear why crypto ransomware is frequently referred to as “data kidnapping.”
What type of ransomware attack is the most threatening?
Out of all the different ransomware attack methods, crypto ransomware is probably the most effective at locking and extracting ransom from users, making it the most threatening in some regards.
Exfiltration presents another serious threat, because not only is the data locked and held for ransom, but there is the potential for sensitive data to leak publically, which may incur additional business and reputational losses.
What are the 4 most used vectors for ransomware?
While there are many types of ransomwares, four of the most used vectors for ransomware are crypto ransomware, exfiltration or leakware, screen lockers, and scareware. Of these four, crypto ransomware and exfiltration pose the most significant threats as they effectively steal your data and hold it hostage unless the owner pays or has a ransomware protection solution in place.
