Subscribe to our blog
Thanks for subscribing to the blog.
April 20, 2022
Topics: Cloud Volumes ONTAP Data ProtectionAWSAdvanced10 minute readSecurity
While AWS provides a number of security options to help users safeguard their data, data encryption may be the most crucial. This key technology can protect critical customer data stored on various AWS solutions.
In this article we’ll take a look at the data encryption options available on AWS, including the server-side encryption methods available on the platform and AWS Key Management Service (KMS).
Data Encryption in AWS
Data typically tends to exist in two states: “at-rest” or “in-transit.” Data “at-rest” is the data that is stored on a storage medium for later access, such as in an AWS S3 bucket, while “in-transit” is data that is in-flight of being transferred from one place to another (such as when an application accesses the data from its at-rest storage for example).
In both cases, if an unauthorized party gains access to your data and it's compromised, there can be irrevocable consequences.
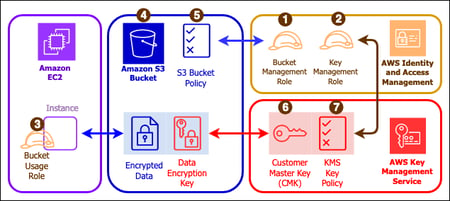 Data at rest encryption architecture for Amazon S3 (Image credit: AWS)
Data at rest encryption architecture for Amazon S3 (Image credit: AWS)
Depending on your application and data, AWS gives customers many options to encrypt their data which complement their identity, resource, and network-based access controls. Many key AWS services can implement data at rest encryption, including Amazon EBS, Amazon S3, Amazon RDS, Amazon Redshift, and AWS Lambda. AWS also provides in-transit data encryption capabilities for solutions such as Amazon SQS to create encrypted communication queues.
To further protect data, AWS also provides flexible encryption key management options including a native AWS Key Management Service and full API capabilities for users to integrate these encryption capabilities to their applications or services. AWS KMS tightly integrates with these services.
AWS At-Rest Encryption Models
It’s important to understand how encryption works before implementing it, for at-rest encryption. The figure below gives us a high-level understanding of the process. A plaintext file uses an encryption key which, after going through an encryption algorithm, results in the plaintext data being encrypted.
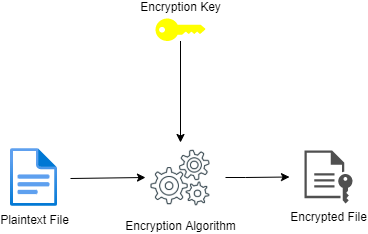 Standard Encryption
Standard Encryption
There are two ways to go about encrypting data at rest on AWS: client-side encryption and server-side encryption.
- Client-side encryption: Encrypts data on the client side and sends the encrypted data to AWS services such as Amazon S3. While customers are in charge of managing the encryption process on their own, depending on the AWS service, customers will typically have two options here when it comes to the handling of the encryption keys:
- Using KMS key stored on AWS KMS
- Using a key stored within the application
- Server-side encryption (SSE): In this method, the backend AWS services or the applications such as Amazon S3 encrypt the data and manage those keys on your behalf. They will encrypt the data as it is written as well as perform the decryption when the data is being read from AWS services such as S3 Storage, AWS EBS, and Redshift.
There are three server-side encryption options available on AWS:
- SSE with customer provided encryption keys (SSE-C): The customer manages the encryption keys while Amazon manages the encryption as well as the decryption. While SSE-C is not supported by all AWS services, Amazon S3 is one of the key services that does support SSE-C.
- SSE with Amazon S3 managed encryption keys (SSE-S3): Typically used for Amazon S3 object encryption, SSE-S3 ensures each object is encrypted using a unique encryption key. As an additional precautionary measure, the key itself is encrypted using a root key that is regularly rotated, providing extra security.
Whenever an S3 object is created or uploaded, the SSE-S3 option can be specified on demand. An Amazon S3 bucket policy can also be leveraged to define SSE-S3 for all the objects stored in the bucket.
- SSE with AWS KMS stored encryption keys (SSE-KMS): While similar to SSE-S3 above, in SSE-KMS the encryption keys are issued and managed by AWS Key Management service itself. This option provides added security compared to SSE-S3 where the access to the KMS service itself requires a different set of access permissions. SSE-KMS is also the most commonly used option across AWS due to its integration with many native AWS services such as Amazon S3, Elastic Block Storage, and AWS Lambda.
Let's take a closer look at Server Side Encryption with AWS Key Management Service below.
What Is AWS KMS?
AWS Key Management Service (KMS) is an AWS managed service that simplifies the creation and the management lifecycle of cryptographic keys that are used for data encryption. AWS KMS provides the tools to encrypt your at-rest data using the AES-256 encryption, which is the industry standard.
Behind the scenes, AWS KMS utilizes a hardware security module (HSM) for protecting and validating keys. It is natively integrated to support many AWS services to meet data encryption requirements. AWS KMS also integrates with AWS CloudTrail for logging the use of KMS keys for audit, regulatory, and compliance purposes.
To understand the main benefits of AWS KMS, it is important to understand some of the key concepts behind the encryption process.
Data keys
Data keys are the encryption keys used to encrypt data sets that are very large. These data keys are normally in plaintext unless encrypted themselves for additional security.
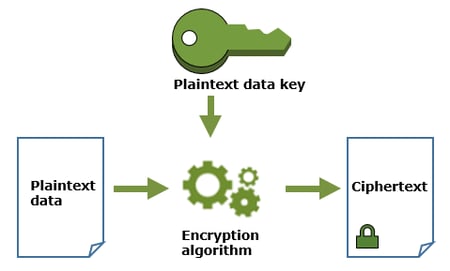
Envelope encryption
Encrypting data is of no use if your encryption keys get stolen. Envelope encryption, as depicted below, is the process of encrypting the plaintext data with a plaintext data key and encrypting that data key with customer master key (CMK) to create an encrypted data key (hence the name “envelope”). The customer master key is also known as the “root key.”
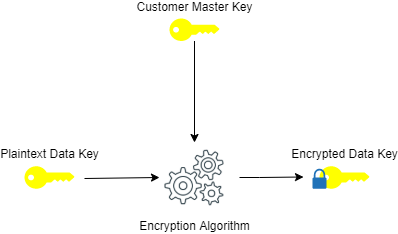
What AWS KMS Does
AWS KMS helps customers protect encryption keys by storing and managing them securely on the AWS cloud. This includes creating data keys as well as encrypting and decrypting these data keys for additional security. When KMS generates a data key, the data key itself is not stored within the KMS (usually returned to you for use outside of the AWS KMS) however the data encryption key can be stored with the data. The KMS key never leaves the KMS environment for security purposes.
The “GenerateDataKey” API command can be leveraged to create a data key on AWS KMS. As a part of the data key creation, AWS KMS will also encrypt a copy of the data key as illustrated below.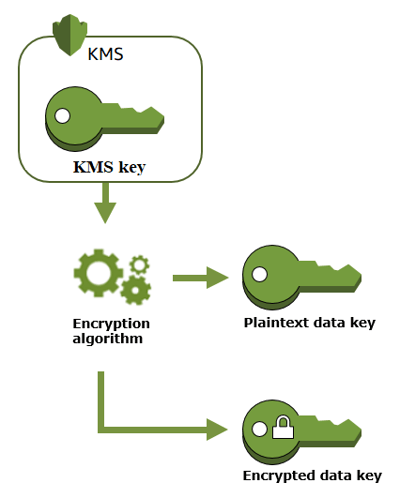
During the envelope encryption process, AWS KMS keys perform the role of a customer master key/root key.
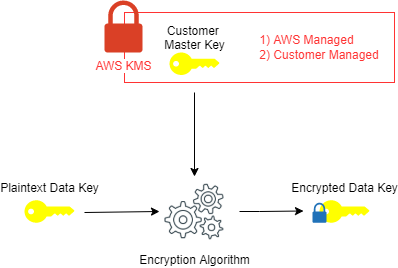
An AWS KMS key can be customer managed or AWS managed:
- AWS Managed: AWS KMS keys generated by AWS services that are integrated with AWS KMS They are usually managed by the AWS services that create them and while the end users can view the AWS managed keys in their accounts, they are unable to perform any management operations such as deletion, change key policies, or their rotation (automatically rotated once every three years).
- Customer Managed: Customers can create keys on AWS KMS which are known as customer-managed KMS keys. These keys are created, owned, and managed by the customers with full control including maintaining the key policies, key rotation, and scheduling the keys for deletion. Customer managed keys usually incur a fee and are counted against the KMS quota per AWS user account.
* In addition to these two key types, there are also AWS-owned keys which is a collection of AWS KMS keys that are owned and managed by AWS that reside within AWS KMS. However, these sit outside the user's AWS account and the user does not have the ability to manage or interact with them. They also don’t count against the user’s AWS KMS key quota.
Server-Side Encryption with AWS KMS (SSE-KMS)
Server-side encryption with AWS Key Management Service provides a simple, secure and a balanced option for many AWS customers who can simplify their encryption tasks such as key generation and root key management tasks. With AWS KMS, encryption and decryption take place in a transparent, independent manner, so you don’t need to make any changes to your application.
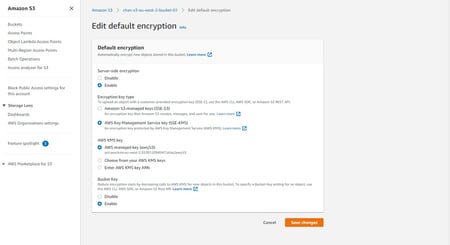
Let's have a look at Amazon S3 as a use case for encryption. When an S3 bucket is created, you can easily specify the use of SSE-KMS as the option to use for the encryption key type and pick AWS managed or your own KMS key option.
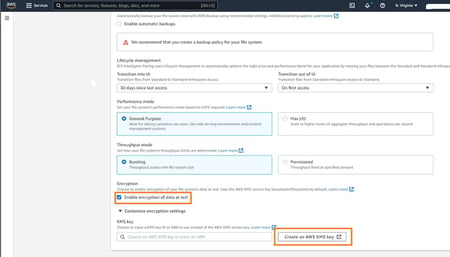
Similarly, Amazon EFS for example also enables users to easily enable data at rest encryption with AWS KMS integration for encryption keys during and after the creation of a new file system.
AWS KMS is often the de-facto choice for many other application services on AWS for at-rest data encryption. It helps customers create and manage KMS keys and track their usage in transactions as well as in audit logs via AWS CloudTrail. It is predominantly used to encrypt data keys themselves. As such, AWS KMS does not store or manage data keys and customers need to use the AWS encryption SDK for data key use.
Users who need to manage their own hardware security modules (HSM) rather than leveraging AWS managed HSMs would need to resort to using custom key store (AKA: CloudHSM) option rather than AWS KMS option. AWS server-Side encryption with KMS operations can also be programmatically invoked via the AWS KMS CLI & AWS KMS API.
Conclusion
With AWS, customers have the choice to leverage both client-side encryption as well as server-side encryption to protect their data. Server-side encryption is often popular and supports three options including customer managed and S3 managed options. However the most convenient and therefore popular server-side encryption option for many customers is leveraging AWS KMS given its versatility and the balanced approach.
For more protection for your AWS workloads, turn to NetApp Cloud Volumes ONTAP. While AWS KMS can help protect your data with encryption, Cloud Volumes ONTAP has a suite of security features to help protect your data beyond the native capabilities on AWS:
- Efficient and immutable NetApp Snapshot technology
- Block-level, incremental forever backup-as-a-service with Cloud Backup
- Seamless failover and failbackdisaster recovery processes
- Role-based access control (RBAC)
- Prevention and recovery solutions against ransomware
- WORM storage immutability
- NetApp Aggregate Encryption (NAE) for data at rest
- NetApp Volume Encryption (NVE)
FAQs
Does AWS encrypt data at rest?
AWS provides data at rest encryption for various AWs services such as Amazon S3, Amazon EBS, Amazon RDS, Lambda and Amazon Elastic File Service.
What encryption does AWS use?
AWS provides both at rest as well as in transit data encryption options for customers to safeguard and protect their data with. There are various encryption options and modes available for customers to choose from, depending on the AWS application and service they’d like to use.
What is SSE-KMS?
Server side encryption with Amazon Key Management Service is one of the most popular encryption options available on AWS cloud. It takes the hassle of encryption key management off the hands of the users who can continue to focus on developing applications on AWS cloud.

