Subscribe to our blog
Thanks for subscribing to the blog.
With the release of NetApp® Astra™ Control 22.04, we are excited to announce support for extending the namespace-as-a-service operational model to application data management. You can now allow the different organizations, teams, or even developers in your company to manage their own application data protection, all from one Astra Control instance.
This separation of namespace-level access control provides the security you need to support multiple organizations or teams within Astra Control. It allows developers to manage the data protection needs of their own applications, without worrying about operational mistakes from other teams. As the account owner, you can even arrange a separate user to have full access or only viewing access, providing granularity for different levels of operators or developers.
For example, let's say that you are a site reliability engineer (SRE) for your company. As shown in the following figure, you are sharing multiple Kubernetes clusters between the continuous integration/continuous deployment (CI/CD) team and the web team, segregating their applications via Kubernetes namespaces. Now, you can give full application data management access to only the namespaces with CI/CD applications to the CI/CD developer. You can also give full access to only the namespaces with web applications to the web admin, without compromising the integrity of the other teams, across clusters. As the SRE, you have access to everything in the environment.
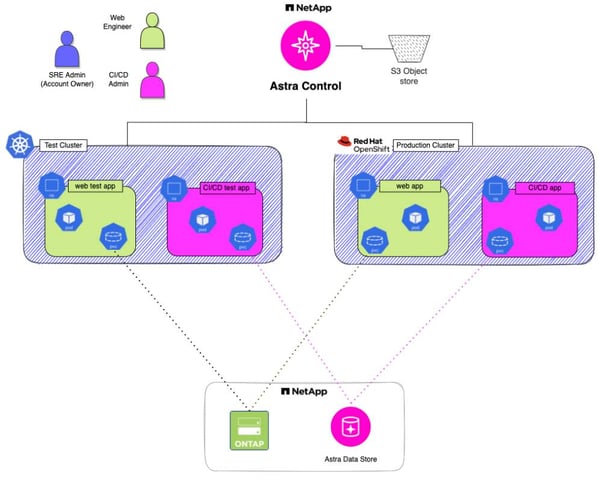
This is cool, but why do I need Astra Control?
Kubernetes does not inherently offer an easy way to perform application data management on its own for microservices-based applications. If you lose your Kubernetes cluster, you may lose your applications and all the data with them. Astra Control not only protects your data, it also protects and restores the application and its metadata along with the persistent volumes, protecting your entire microservices-based application and its volumes as one entity.
Astra Control provides data protection with application and data snapshots. It accomplishes disaster recovery with full backups and restoration of your application and its metadata along with its persistent volumes. It also provides application and data portability with instant active clones. Now, with the namespace-as-a-service operational model, you can manage applications from different organizations with one Astra instance, allowing individuals access to application data management of only their specific organization or team.
What are Kubernetes namespaces And what is the namespace-as-a-service model?
Namespaces (or projects in OpenShift Container Platform) are Kubernetes objects that provide separation between objects and resources in a shared Kubernetes cluster. Namespaces (or OCP projects) are often used to isolate applications or even teams from each other while allowing the deployed applications to share cluster resources, like CPU and memory. You can also limit cluster resources per namespace by using resource quotas to prevent objects in any one namespace from using all the compute resources available on the worker nodes.
Some resources, such as pods, PersistentVolumeClaims (PVCs), secrets, etc., are namespace scoped. Other resources, such as nodes, StorageClasses, PersistentVolumes (PVs), etc., are seen as cluster-wide resources and thus are not namespaced. Even though PVs are not namespaced, they are bound to a namespaced PVC. Therefore, as long as a team or developer has access to a specific namespace within Astra Control, they will also be able to provide data management to any PVs bound to a PVC within that namespace.
The Astra Control namespace-as-a-service operational model allows an overall administrator or account owner to give namespace-level Astra Control access to a specific team, admin, or developer. That user has viewing or administrative access and can provide application data management to all resources only within that specific namespace or namespaces. They do not have visibility into the application namespaces of other teams. The account owner has access to the whole cluster and/or can provide individual access to users based on their requirements.
As an account owner with full Astra admin rights, can you give me an example on how to set this up?
Sure thing. Although we will use Astra Control Center as an example, the same applies to Astra Control Service. We will show the UI, but of course everything can be done via the API as well. If you'd prefer to watch a video that uses the UI, see Astra Control Namespace as a Service.
Let's say that you have a web tennis shop located in a namespace called ntap-tennisgalore. You want the web team to control the application data management for that shop. The web team has the application deployed on two Kubernetes clusters, one for test and one for production. You have used the key team to denote who owns each namespace and labeled the tennisgalore namespaces team: web. (Hint: Use the command kubectl label namespace <namespace-name> <key>=<value> to label the namespaces in a Kubernetes cluster.)
Simply log into Astra on an account with full rights. From the main dashboard, select Add New User, as shown in the following screenshot.
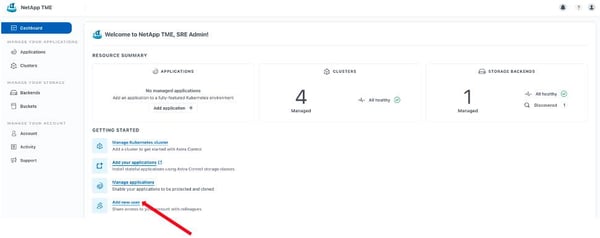
Next, enter the details and then select a User Role from the dropdown menu. To give this person full rights to the namespace, select Member. To give them only viewing rights, select Viewer. Next, check Restrict Role to Constraints and Add Constraint.
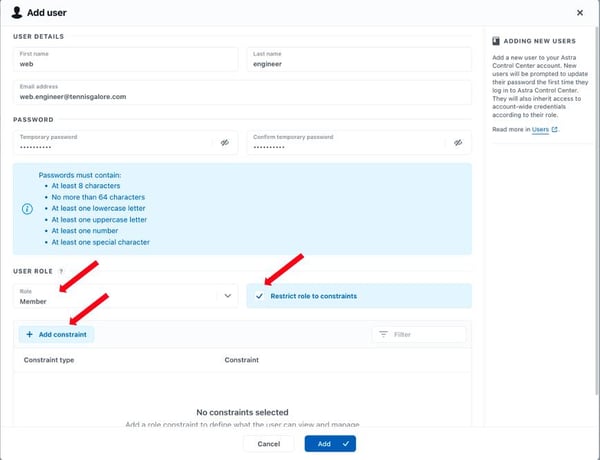
You can perform the constraint on one or more namespaces, or you can select one or more namespace labels from the dropdown menu.
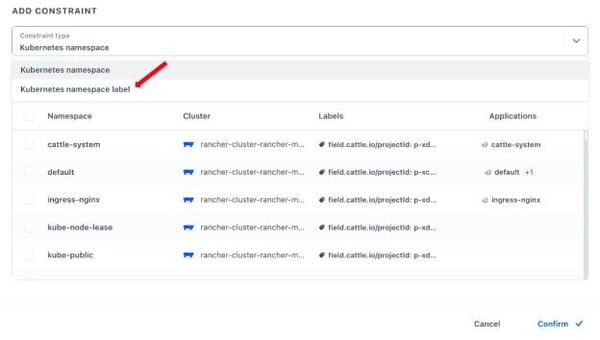
Using labels is a way to select numerous namespaces at once. In this case you used the key team with the value web to form the label team:web to identify the namespaces running the web application. Select it as shown in the following screenshot.
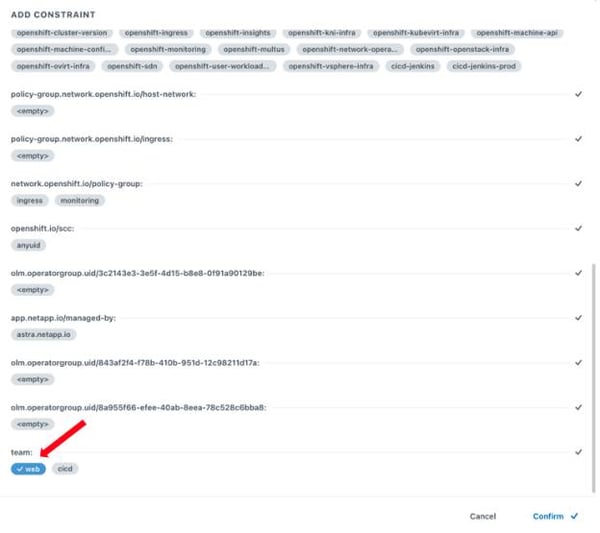
Select Confirm and press Add. Now the user web.engineer@tennisgalore.com can log in with the temporary password that you generated. They need to change their password upon initial login.
Now, the user has access to only the namespaces with the web application (or namespaces with the team:web label). They can perform application data management on those namespaces, without viewing or accessing other teams’ applications and data. Also, they don’t have visibility into the back end, and they can’t add users.
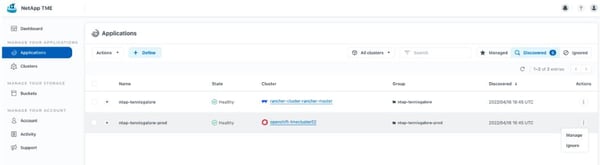
Now the web team can set up and manage their own application data management for the store, and you can get back to doing the fun stuff. Sweet!
This is cool, how can I try it out?
Download the new version of the self-managed Astra Control Center free trial, or sign up for the fully managed Astra Control Service free plan. Install it in your lab or try it in the cloud to get application data management for all your Kubernetes applications.
Please let us know how it goes. You can reach us at astra.feedback@netapp.com. We'd love to hear from you!