Subscribe to our blog
Thanks for subscribing to the blog.
March 15, 2022
Topics: Cloud Insights Data ProtectionDisaster RecoveryAdvanced7 minute readRansomware ProtectionSecurity
Given the number of high-profile ransomware attacks over the years, and the grave consequences of an infection, you might think that prevention methods should be maturing to the point that ransomware will soon be stamped out entirely.
Consider the once ubiquitous threat of exploit kits, such as the infamous Angler, a massive headache for any security team at the time. These exploit kits have all but faded from memory, thanks to the relentless effort by researchers to clamp down on them.
But ransomware is still everywhere, and total prevention of ransomware is effectively impossible. Let us count down the reasons why that is so.
5: It Pays
Attackers are more motivated than ever because successful attacks offer huge payoffs. The average ransom paid by organizations in the US, Canada, and Europe increased from US$115,123 in 2019 to $312,493 in 2020—a 171% year-over-year increase. The average for Q1 2021 came in at $850K. Ransomware-related incidents have increased by 65% over 2019. In addition, the attack frequency will continue to grow, from an attack every 11 seconds to an attack every 2 seconds by 2031. These attacks will continue to be increasingly commonplace. With numbers like these, it is easy to see why ransomware continues to be a favorite criminal endeavor.
And even though law enforcement agencies advise against it, organizations keep paying the ransom. It’s natural for companies to want to protect their business. The cost of the disruption to the business often eclipses the ransom itself, which means that paying up is often the most cost-effective option.
4: It’s Easy
On the flip side, the out-of-pocket costs to run a ransomware campaign are low. Today, an attacker can buy a prefabricated ransomware kit for a relatively paltry sum. The kit contains everything needed to deploy and monetize an attack, including encryption services, the payload dropper, and obfuscation tools. A typical ransomware-as-a-service (RaaS) subscription starts from as low as $100 per month. More complex and powerful variants can cost thousands, but the payoff potential increases as well. Support plans are also included to ensure that attackers can extract the maximum value from the service.
3: It’s Proven Effective
Ransomware is a profitable business, forget the stereotype of hoodie-wearing malefactors in dark rooms; this is a sophisticated network comparable to any corporate partner program.
One of the latest examples of Ransomware as a Service (RaaS) is DarkSide, which was first found at the beginning of August 2020 and moved to a RaaS distribution model by November. The typical ask is between $200K to $2M for keys to unlock your data based on incidents reported. Not only are DarkSide ransomware operators getting large paydays, but they are also positioning themselves as being “Robin Hood” as they take money from large profitable corporations and have been known to make charitable donations from the proceeds.
Reports based on the leak sites indicate there are at least 90 victims affected by DarkSide to date. In total, more than 2 TB of stolen data is currently being hosted on DarkSide sites further demonstrating another incentive to pay up.
2: It Has a Rapid ROI
Another reason that ransomware is so attractive is that once it makes its way inside an organization, typically via email attachments, malicious URLs, insecure Remote Desktop Protocols, or malvertising, it moves fast. It scans the network to locate files, then encrypts the content and demands a ransom. Unfortunately, once the encryption process gets going, there is little that can undo it.
And in an alarming trend, a new methodology has arisen by which attackers steal data before encrypting it. In May 2021, Colonial Pipeline, supplier of 45% of the fuel for the US east coast, was hit with a ransomware attack. The attack was carried out by Darkside or an affiliate. In addition to locking Colonial Pipeline’s computer systems, DarkSide also stole over 100 GB of corporate data. This data theft shows that the group has a history of doubly extorting its victims, not only asking for money to unlock the affected computers but also demanding payment for the captured data, while threatening to publicly leak the stolen data if the victims do not pay.
So, it is hardly a shock that attackers continue to pursue this vector. It is lucrative and easy to pull off, and people keep on paying.
1: People are Unreliable
So far, we have covered why ransomware is so ubiquitous, but nothing about how to stop it. Although it is true that a considerable number of attacks could be prevented by better patching hygiene, there is one reason above all others that total prevention is impossible, and that’s people.
You trust that your employees would never intentionally harm your organization. But ransomware infections still happen because employees are not hyperalert at all times to the dangers of malicious emails or phishing attempts.
I am sure that many readers are familiar with regular mandatory security-awareness computer-based training. Training certainly does not hurt, but even your most security-aware employees can have a momentary lapse in judgment and click a link in a seemingly innocuous email. And without hyper restrictive security policies that get in the way of people actually doing their jobs, that lapse in judgement is all it takes.
Zero Trust Ransomware Protection
If you can’t prevent ransomware, what can you do to protect against it?
Your employees need access to data to do their jobs just like ransomware does, so your employees become the attack vector. Policies and roles that restrict access to data can help, but too many of them can get in the way of productivity.
The answer is early detection, user behavior analysis, and automated action when suspicious patterns occur. Detection is needed within seconds, not minutes, hours or longer.
NetApp® Cloud Insights offers just this type of detection with a feature called Cloud Secure. With Cloud Secure you can monitor activity, detect anomalies, and automate responses.
- Monitor user activity
To accurately identify breaches, every user activity across on-premises and hybrid cloud environments is captured and analyzed. The data is collected using a lightweight data collector agent, installed on a VM (Virtual Machine) in the customer’s environment. This data also includes user data from Active Directory and LDAP (Lightweight Directory Access Protocol) servers and user file activity from ONTAP storage, either in your own datacenters or in the cloud.
Cloud Secure detects anomalies in user behavior by building a behavioral model for each user. From that behavioral model it detects abnormal changes in user activity and analyzes those behavior patterns to determine whether the threat is ransomware or a malicious user. This behavioral model reduces false positive noise.
- Detect anomalies and identify potential attacks
Today’s ransomware and malware are sophisticated, using random extensions and file names, which makes detection by signature-based (blocked list) solutions ineffective. Cloud Secure uses advanced machine learning algorithms to uncover unusual data activity and detect a potential attack. This approach provides dynamic and accurate detection and reduces false detection noise.
- Automate response policies
Cloud Secure alerts you to a potential ransomware attack and provides multiple automatic response policies to protect your data from the attack.
- Takea data snapshot when it detects unusual behavior, making sure that your data is protected so that you can recover quickly, whilst limiting any potential for disruption from a false positive.
- Block a user’s ability to access data:
- When abnormal (read/write) user behavior is detected.
- When unusual file deletion behavior is detected.
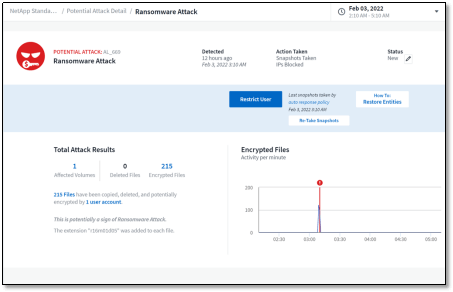
Cloud Secure dashboard showing ransomware attack
Cloud Secure provides detailed access auditing, so administrators can quickly identify compromised data along with the source of the attack for quick remediation and recovery.
If you are interested in learning more about Cloud Secure, a part of Cloud Insights, start by signing up for our 30-day free trial.