What Is the Data-Centric Approach to Ransomware Protection?
A complete guide to the principles and tools

A complete guide to the principles and tools


Ransomware continues to be the most serious threat to enterprises, and organizations are realizing that the traditional ransomware protection method of securing the network and relying on backups just doesn’t cut it anymore. More often than not, successful ransomware attacks still take place after networks are secured.
A truly comprehensive security posture needs to protect not only the network, but also the asset. The ransomware ultimately wants to target—your data. This is what is known as a data-centric approach to ransomware protection.
This guidebook will give you a full review of ransomware threats and what you can do to create a data-centric protective stance using NetApp Ransomware Protection.


Ransomware is a form of malicious code that locks users out of their data. Once the data is locked, the attacker demands a ransom to unlock the data.



According to the Allianz Risk Barometer of 2022, cyberthreats now rank as the top business risk for enterprises, with ransomware being the most concerning cyberthreat to a business.
Breaches
Incidents

85%
of breaches involved a human element
10%
of breaches involved ransomware, doubling last year's frequency



Part 2
There are two main ways that enterprises have sought to protect themselves against ransomware attacks, allowing them to recover locked data:
Perimeter Protection
Backup Solutions
There is no guarantee that protecting the network will ensure ransomware infections won’t take place.
Building a good defensive wall is an idea as old as the foundations of civilization itself and the basis of perimeter protection: Tighten access to your network to ensure no infections can enter.
Any wall can be breached. Ransomware perimeter protection is constantly challenged by a large range of ever-changing malware injection techniques and doesn’t work against threats that may already be inside the system, lying in wait to deploy malicious code.
backup data is as vulnerable to infection as the rest of your data.
Backups are the last line of defense in ransomware attack situations. If data becomes inaccessible after a ransomware attack, an up-to-date backup copy can allow systems to be restored.
Backups are not aware of attacks, and so are vulnerable to them. The latest strains of ransomware recognize it is crucial to find and lock backups alongside the primary dataset. And so an attack might wait until the backup is effectively neutralized, ensuring that the victim has no other option than to pay up.




Part 3


While all cyber attacks can be damaging, ransomware attacks disrupt an organization’s most valuable asset: their data.

Centralized file storage solutions are a particularly attractive target for ransomware actors.

The network is not the target of a ransomware attack. The best security stance to combat ransomware is at the data level.



Ultimately, the security of your company is a responsibility that every member of the organization shares, but when it comes to protecting data, it’s integral to the IT role.

This responsibility goes far beyond the traditional data protection tasks of backing up and restoring data.

This responsibility goes far beyond the traditional data protection tasks of backing up and restoring data.
At NetApp, we’ve been providing industry-leading data management solutions for decades. That’s why we understand data protection better than anyone and are perfectly positioned to offer the most comprehensive suite of tools to protect your data.

This responsibility goes far beyond the traditional data protection tasks of backing up and restoring data.

This responsibility goes far beyond the traditional data protection tasks of backing up and restoring data.
Netapp Ransomware Protection is a comprehensive set of data-centric capabilities, allowing you to protect your data estate with a zero trust approach from the inside out. It enables you to map and classify your data, detect abnormal user activity, manage access, and avoid costly downtime with rapid backup and restore.

This responsibility goes far beyond the traditional data protection tasks of backing up and restoring data.

This responsibility goes far beyond the traditional data protection tasks of backing up and restoring data.
This dashboard provides your IT teams with insights into the cyber resiliency posture of their entire on-prem and cloud data estate. The dashboard also offers a single interface to multiple ransomware protection tools. The dashboard additionally scores your system’s cyber resiliency and readiness with built-in best practice recommendations.

This responsibility goes far beyond the traditional data protection tasks of backing up and restoring data.

This responsibility goes far beyond the traditional data protection tasks of backing up and restoring data.






Part 4
In a data-centric context, cyber resilience is centered around the state of the data itself, with the overall system’s wellbeing built from the data outward.




The goals for cyber resilience aren’t specific to ransomware. Exploring and applying them in a data-centric context sets the required capabilities apart from the traditional security mechanisms and enables us to significantly increase the security posture of the organization. A core part of understanding a data-centric security posture is to consider how cyber resilient systems are built.
As defined by the National Institute for Standards and Technology (NIST) in “Ransomware Risk Management: A Cybersecurity Framework Profile”, cyber-resilient systems include five functions in their framework:

Manage cybersecurity risk to systems, assets, data, and capabilities

Safeguard to ensure delivery of services
Identify the occurrence of a cybersecurity event

Take action regarding a detected cybersecurity event

Maintain plans for resilience and restore any capabilities or services that were impaired due to a cyber-security event



The airbags, seat belts, crush zones, car seat attach points, rollover strength, and side impact protection— the most important safety features of a car — are all designed with one thing in mind: to keep the people inside the car safe.
Some features, like proximity sensors, are there to make sure those features never need to be utilized, but no one gets into a car relying just on those sensors.
Data-centric cyber resilience is designed the same way—with your data as the number one priority.
The airbags, seat belts, crush zones, car seat attach points, rollover strength, and side impact protection— the most important safety features of a car — are all designed with one thing in mind: to keep the people inside the car safe.
Lorem Ipsum is simply dummy text of the printing and typesetting industry. Lorem Ipsum has been the industry's standard dummy text ever since the 1500s, when an unknown printer took a galley of type and scrambled it to make a type specimen book.
Data-centric cyber resilience is designed the same way—with your data as the number one priority.
The airbags, seat belts, crush zones, car seat attach points, rollover strength, and side impact protection— the most important safety features of a car — are all designed with one thing in mind: to keep the people inside the car safe.
This is content related to Crush Zone's. Lorem Ipsum 3 is simply dummy text of the printing and typesetting industry. Lorem Ipsum has been the industry's standard dummy text ever since the 1500s.
Data-centric cyber resilience is designed the same way—with your data as the number one priority.
The airbags, seat belts, crush zones, car seat attach points, rollover strength, and side impact protection— the most important safety features of a car — are all designed with one thing in mind: to keep the people inside the car safe.
This is content related to Car Seat Attachments. Lorem Ipsum is simply dummy text of the printing and typesetting industry. Lorem Ipsum has been the industry's standard dummy text ever since the 1500s
Data-centric cyber resilience is designed the same way—with your data as the number one priority.
The airbags, seat belts, crush zones, car seat attach points, rollover strength, and side impact protection— the most important safety features of a car — are all designed with one thing in mind: to keep the people inside the car safe.
This content is related to Rollover strength. Some features, like proximity sensors, are there to make sure those features never need to be utilized, but no one gets into a car relying just on those sensors.
Data-centric cyber resilience is designed the same way—with your data as the number one priority.
The airbags, seat belts, crush zones, car seat attach points, rollover strength, and side impact protection— the most important safety features of a car — are all designed with one thing in mind: to keep the people inside the car safe.
This content is related to Side Impact Protection. Some features, like proximity sensors, are there to make sure those features never need to be utilized, but no one gets into a car relying just on those sensors.
Data-centric cyber resilience is designed the same way—with your data as the number one priority.











Approach begins with data at the center, it starts from the innermost levels of data protection and then moves outward from level to the next.

Understanding what data you have and how it should be protected is key in ransomware defense.

Your data attributes define who can access your data and what they can do with it.

Continuously analyzing the behavior of how users and systems use your data allows you to detect when something is not right.

Data storage capabilities allow you to respond and recover when ransomware is detected to ensure business continuity.
Understanding and adopting industry cyber resiliency best practices across the board provides a holistic approach to your protection strategy.













Use Data Sense’s governance capabilities to better understand what information is stored in your data estate. Locate the most sensitive information using AI-driven analysis engines that categorize and classify your data. With this information, you can continuously make the right adjustments to properly secure your data and mitigate the risks involved with ransomware.
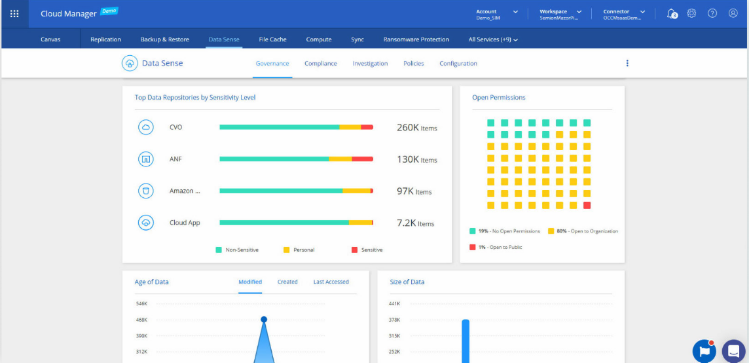

Part of our governance capabilities includes constant insights into your first level of defense: file and folder level permissions. With “Data Sense” permissions analysis, enhanced filtering capabilities, and auditing, you can tighten your security and ensure the right people get access to the right data, at the right level.
Based on access permissions set across your data estate, data gets created only where it’s allowed, and that includes files encrypted by ransomware during an attack. With ONTAP’s file access notification framework (FPolicy), you can block file creation and other operations based on known ransomware file extensions. This policy can be implemented even if an attacking user or computer instance has write permissions to folders.


Using machine learning capabilities, ONTAP is able to identify, prevent, or limit sophisticated ransomware attacks by continuously analyzing workloads (available from ONTAP 9.10.1). This anti-ransomware feature uses workload analysis in NAS (NFS and SMB) environments to proactively detect and warn about abnormal activity that could point to a ransomware attack. When the system detects an attack, anti-ransomware creates a new Snapshot copy in addition to the ongoing protection from scheduled snapshots.
Ongoing user behavior analytics (UBA) is required to identify, prevent, or limit sophisticated ransomware attacks. NetApp’s UBA capability tracks the behavior of individual users and communities to identify typical data access patterns. It then reports when behavior differs from the normal observed pattern. In such cases, UBA can proactively respond by denying access to files and folders where suspicious activity is taking place and take further actions to protect your data using Cloud Secure and FPolicy external mode.
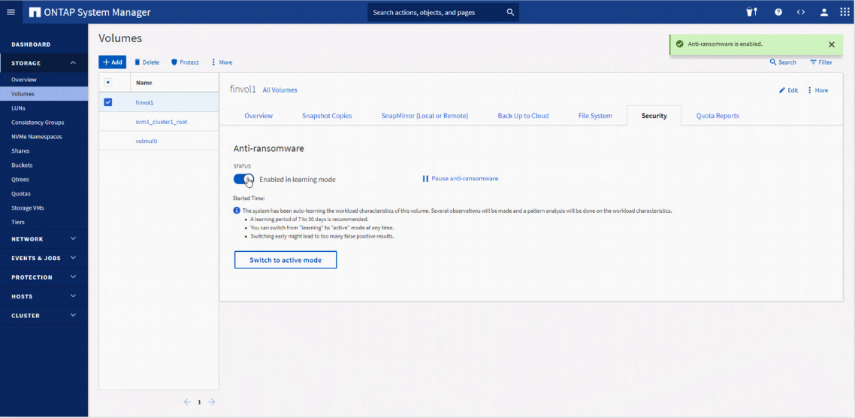
Data stored in ONTAP systems is protected by Snapshot, which is a point-in-time, read-only image of your data that shows exactly what your data looked like the moment the snapshot was taken. Since Snapshot images are read-only, captured data can’t be encrypted and locked by ransomware. With the FlexClone and SnapRestore features, you are able to restore an entire volume or individual files from a snapshot in the event of a ransomware attack, significantly faster than with any other possible recovery method.
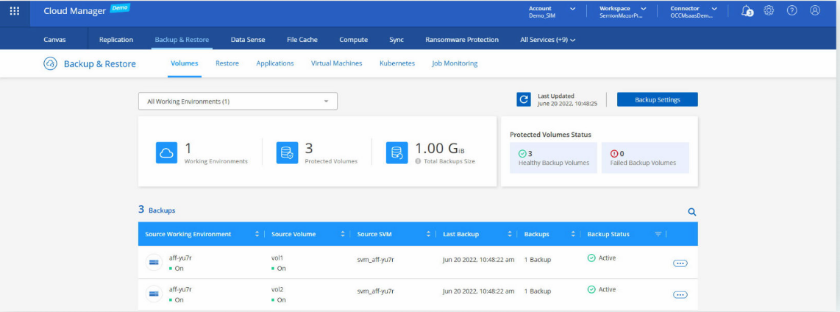
Immutable backups, such as those provided by NetApp Cloud Backup, help bring your business back online without having to pay heavy ransoms in the event of an attack. With immutable backups, you can honor customer SLAs and recovery point objectives. Cloud Backup’s incremental forever backups on the block level provide faster restores that are more cost-efficient than any other backup solution on the market.
To add another layer to your data protection strategy, data can be easily and efficiently replicated to a different geographic location. These data recovery sites can be created with Cloud Volumes ONTAP or Amazon FsX for NetApp ONTAP. Since NetApp’s data replication engine replicates your immutable snapshots, your secondary copy is protected and can also be used to recover from attacks. Entire snapshots or individual files can be replicated back to the original location or, in a worst-case scenario, you can failover to your data recovery site and work on a ransomware-free copy of your data.
Air-gapped backups prevent malicious activities from accessing your additional copy of the data. By creating a WORM (Write Once Read Many) volume, SnapLock prevents your production data and snapshots from being tampered with, resulting in a logical air gap of your data that is quickly accessible, safe from deletion, and immutable.
Your Active Directory retains a lot of information and is responsible for many functionalities of your domain assets including resource allocation, authentication, authorization, and more. Therefore, it’s a “holy grail” for infiltrators who use it to gain access, escalate privileges, and collect information on your network. It’s important to constantly monitor your Active Directory with tools like Data Sense to find anomalous activities or unnecessary privilege allocations and remove possible security gaps that exist.

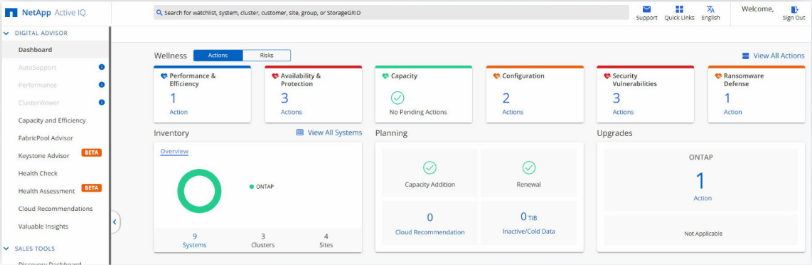
NetApp provides built-in tools to help detect ransomware in early stages. For ONTAP in particular, these tools include Active IQ Unified Manager and Active IQ Digital Advisor. These tools alert about abnormal Snapshot copy and volume growth rates, and loss in storage efficiency, which may indicate an ongoing ransomware attack. They also alert when there are snapshot creation failures and unconfigured security capabilities, such as FPolicy.
NetApp also offers a dedicated Ransomware Protection Dashboard in Cloud Manager that allows you to respond to threats in real time. This dashboard provides your IT teams with insights into the cyber resiliency posture of their entire on-prem and cloud data estate. The dashboard also offers a single interface to multiple ransomware protection tools. The dashboard additionally scores your system’s cyber resiliency and readiness with built-in best practice recommendations. This allows you to identify problem areas without the overhead of searching for them on your own. IT teams can use these advanced defense mechanisms to ensure your most critical data is protected and to strengthen cyber resilience.



At NetApp, we’ve been providing industry-leading data management solutions for decades. That’s why we understand data protection better than anyone and are perfectly positioned to offer the most comprehensive suite of tools to protect your data.
Netapp Ransomware Protection is a comprehensive set of data-centric capabilities, allowing you to protect your data estate with a zero trust approach from the inside out. It enables you to map and classify your data, detect abnormal user activity, manage access, and avoid costly downtime with rapid backup and restore. IT teams can use these advanced defense mechanisms to strengthen your cyber resiliency and make sure your most critical data stays protected.
